Udacity Quizzes
The Security Mindset
Security Impact Quiz

Security Impact Quiz Solution
Black Market Prices Quiz

Black Market Prices Quiz Solution

Sony Pictures Quiz
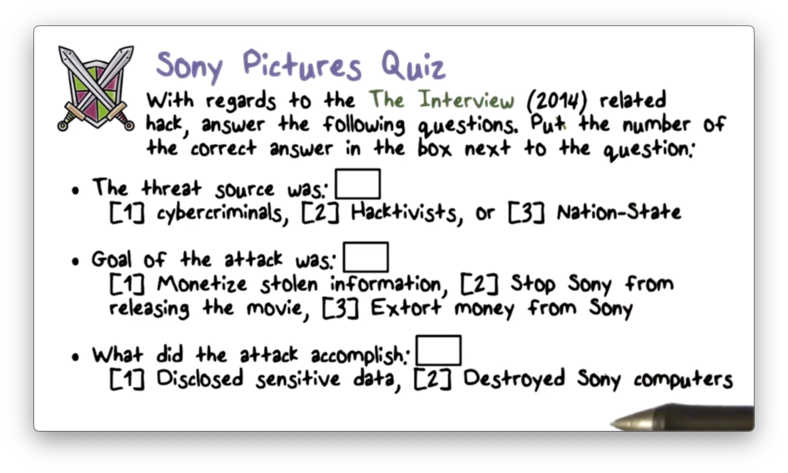
Sony Pictures Quiz Solution

Security Requirements Quiz

Security Requirements Quiz Solution

Losses Due to Cyber Crime Quiz

Losses Due to Cyber Crime Quiz Solution

Security Mindset Quiz

Security Mindset Quiz Solution

Software Security
Stack Access Quiz
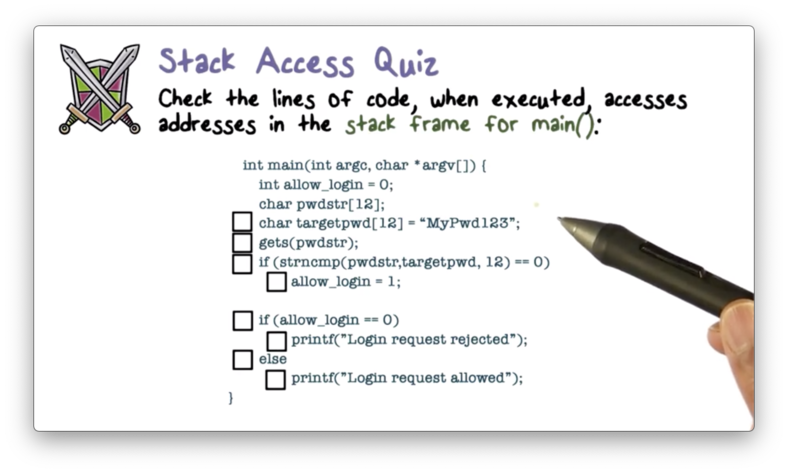
Stack Access Quiz Solution

Attacker Code Quiz

Attacker Code Quiz Solution

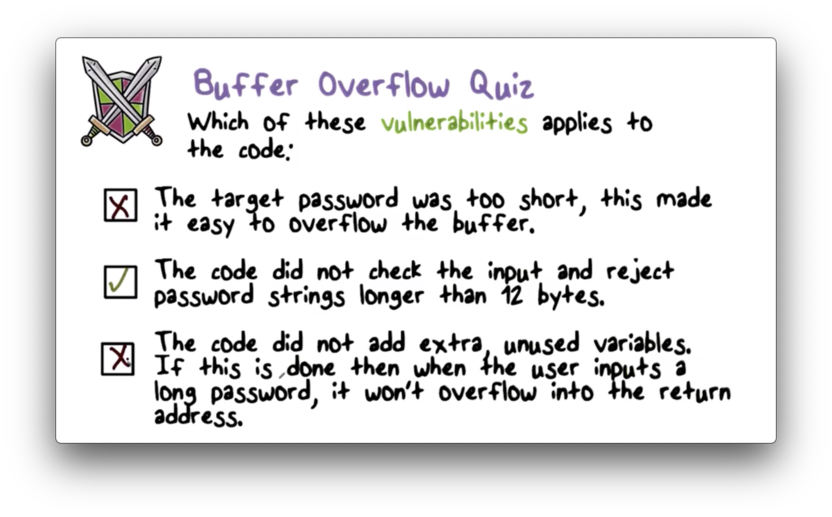
Buffer Overflow Quiz

Buffer Overflow Quiz Solution
NVD Quiz
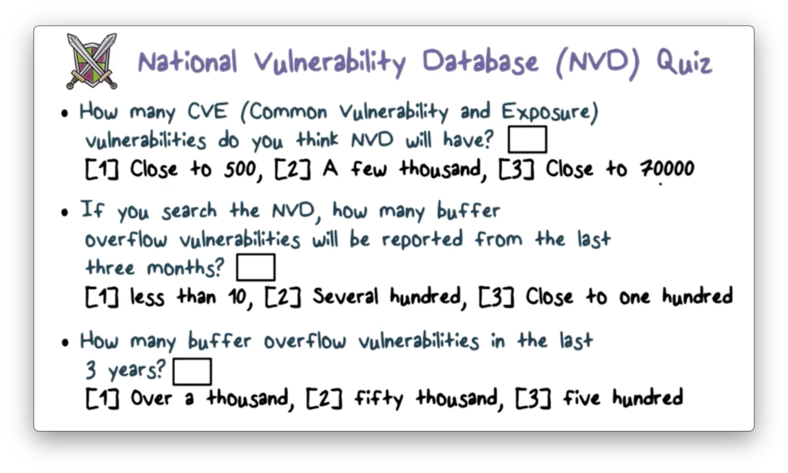
NVD Quiz Solution

Strongly Vs Weakly Typed Language Quiz

Strongly Vs Weakly Typed Language Quiz Solution

Buffer Overflow Attacks Quiz

Buffer Overflow Attacks Quiz Solution

Operating System Security
Secure OS Quiz 1

Secure OS Quiz 1 Solution

Secure OS Quiz 2

Secure OS Quiz 2 Solution

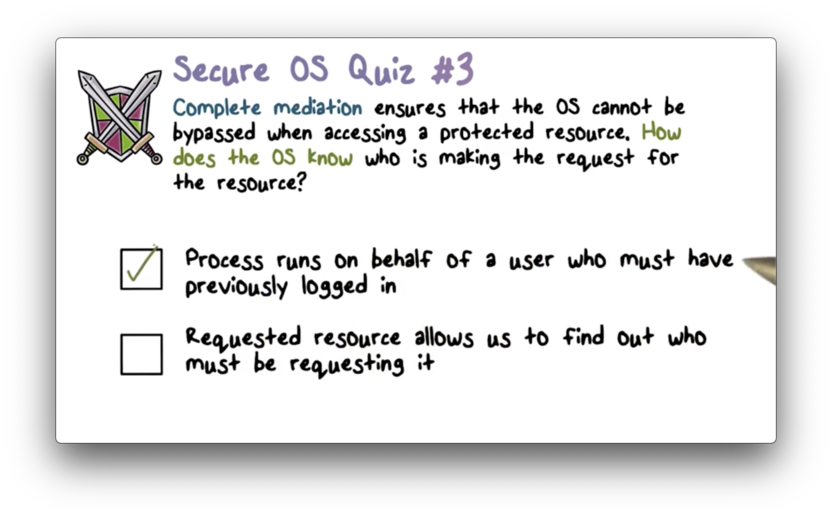
Secure OS Quiz 3

Secure OS Quiz 3 Solution
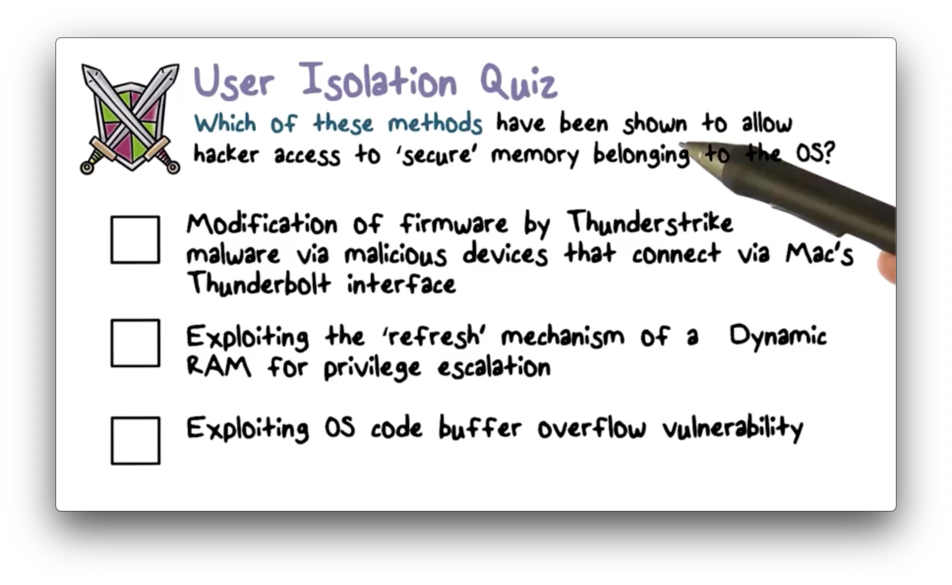
User Isolation Quiz
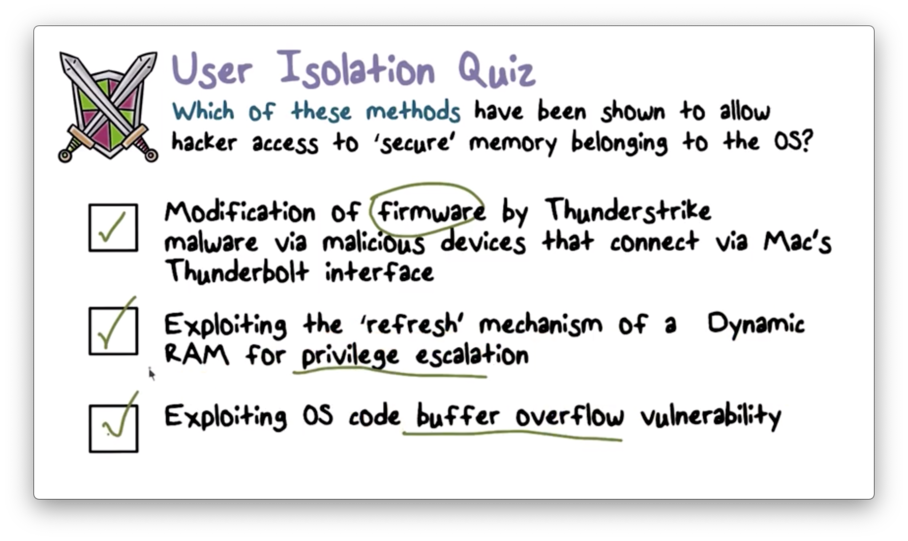
User Isolation Quiz Solution
Revisiting Stack Overflow Quiz

Revisiting Stack Overflow Quiz Solution

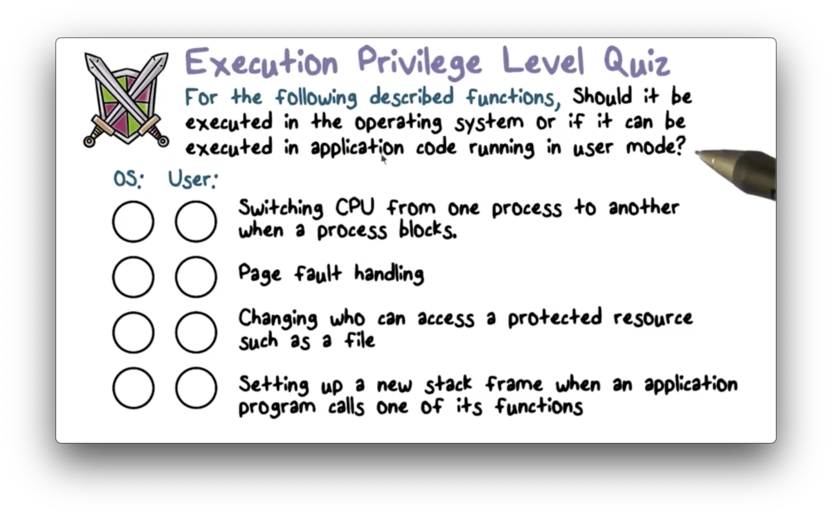
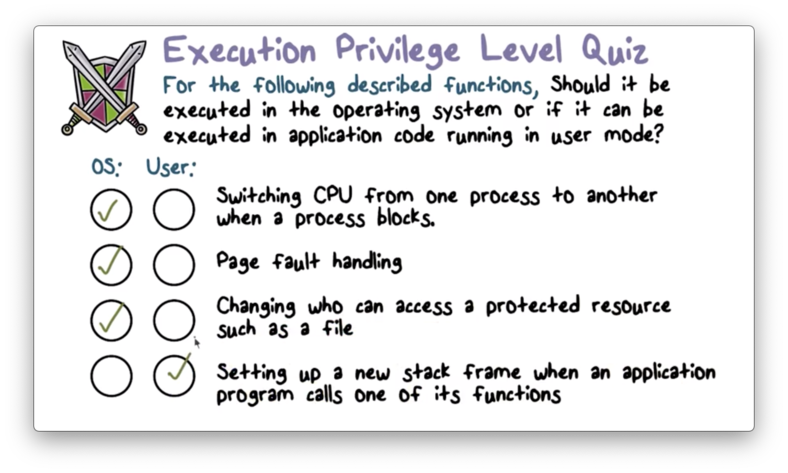
Execution Privilege Level Quiz
Execution Privilege Level Quiz Solution
TCB Requirements Quiz
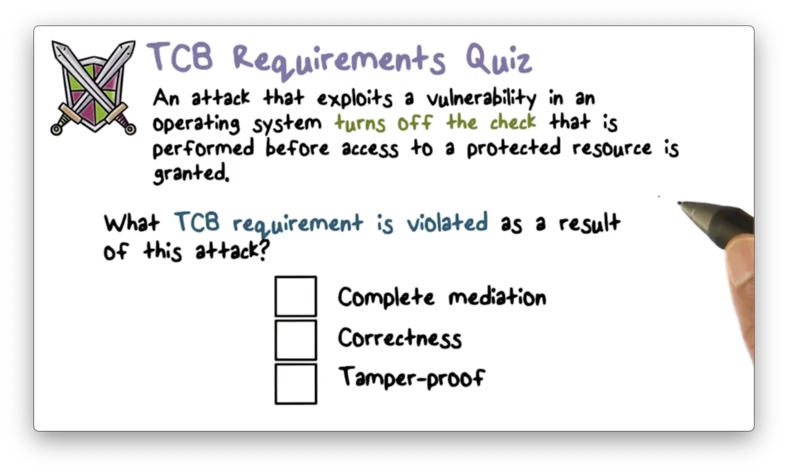
TCB Requirements Quiz Solution

Size of Security Code

Size of Security Code Solution

Hypervisor Code Size Quiz

Hypervisor Code Size Quiz Solution

Authentication
Authentication Quiz

Authentication Quiz Solution

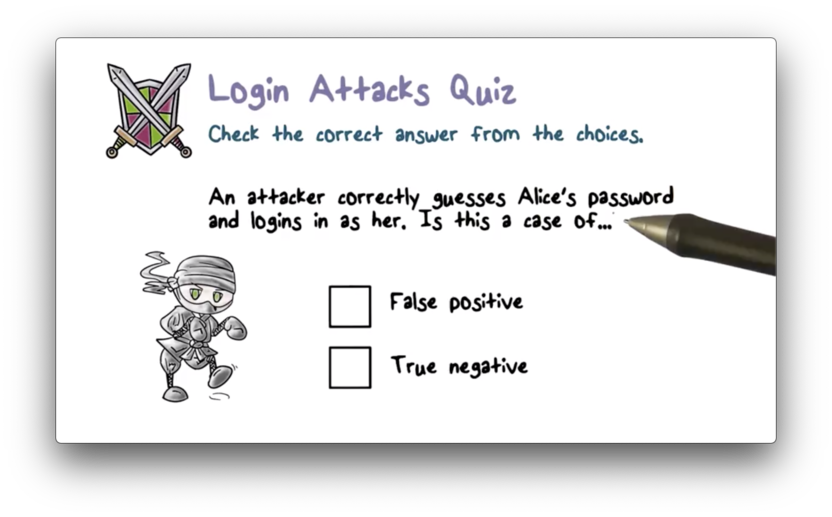
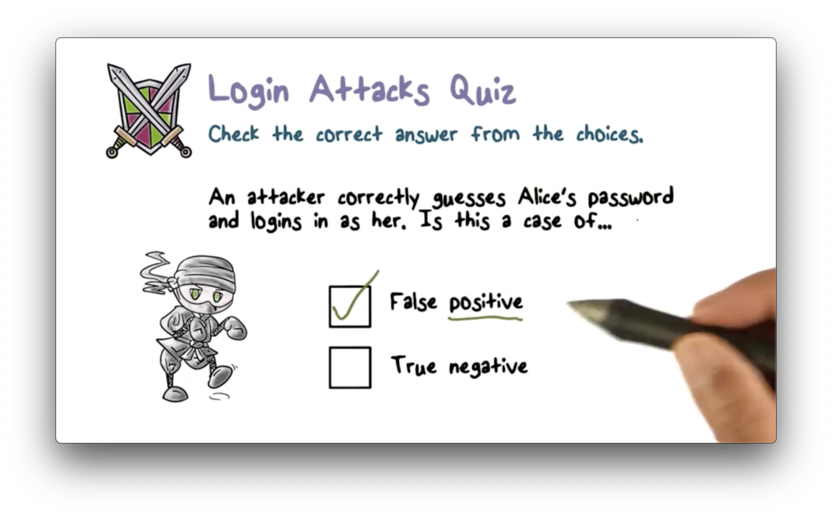
Login Attacks Quiz
Login Attacks Quiz Solution
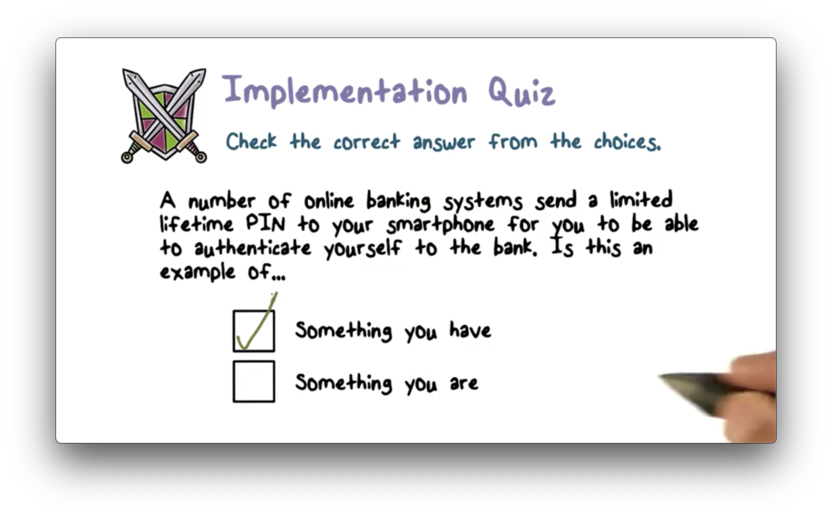
Implementation Quiz

Implementation Quiz Solution
Password Popularity Quiz

Password Popularity Quiz Solution

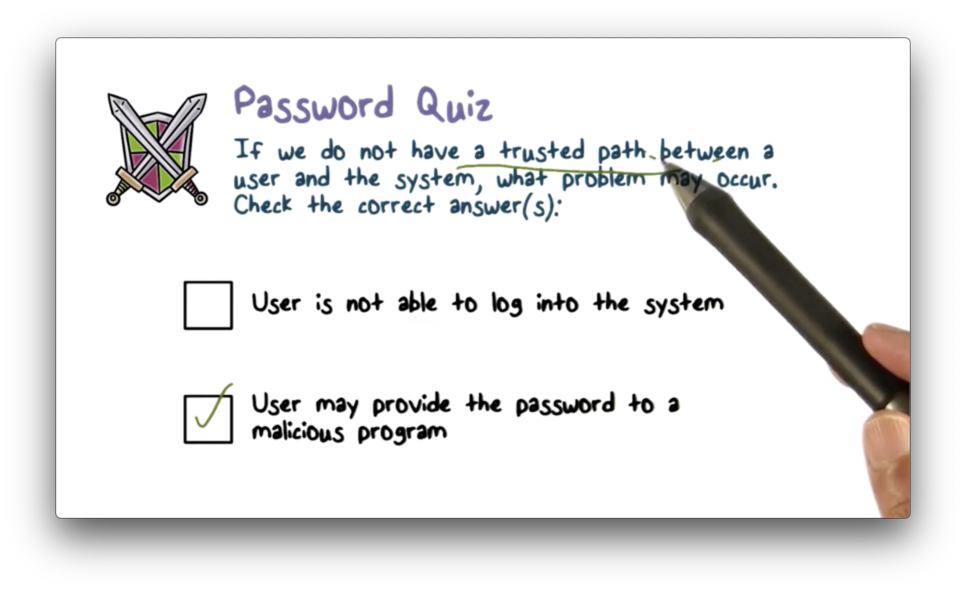
Password Quiz

Password Quiz Solution
Hashed Passwords Quiz

Hashed Passwords Quiz Solution

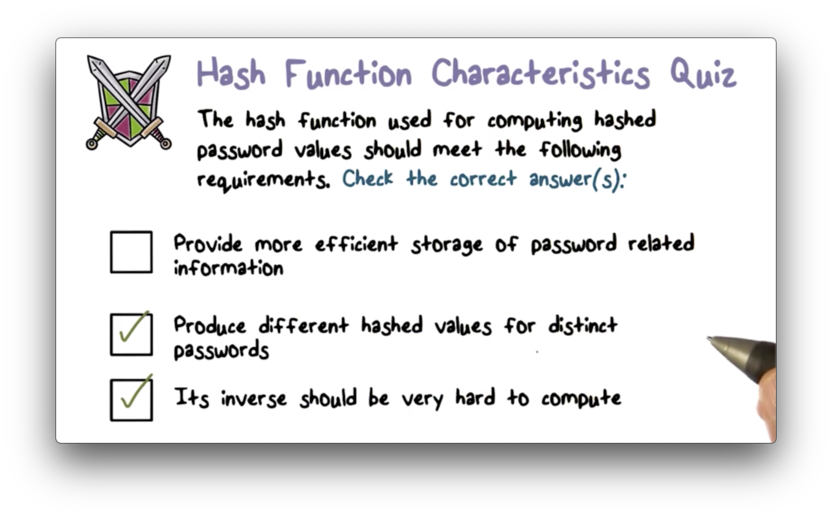
Hash Function Characteristics Quiz
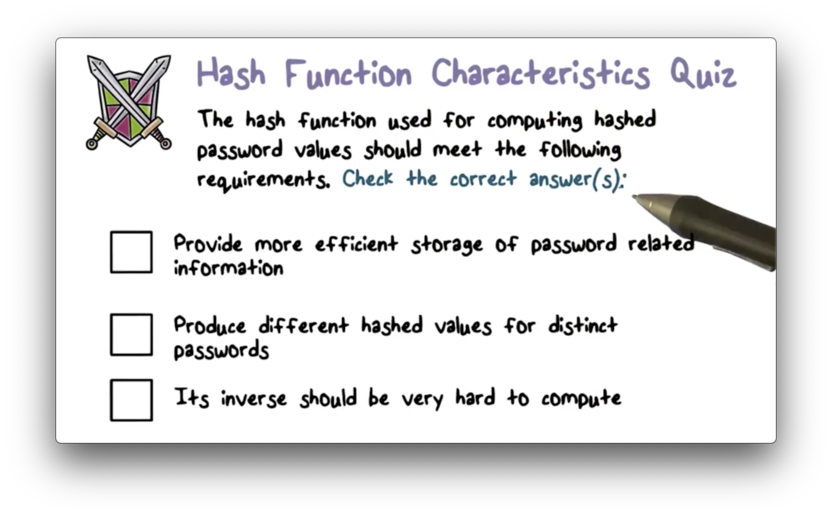
Hash Function Characteristics Quiz Solution
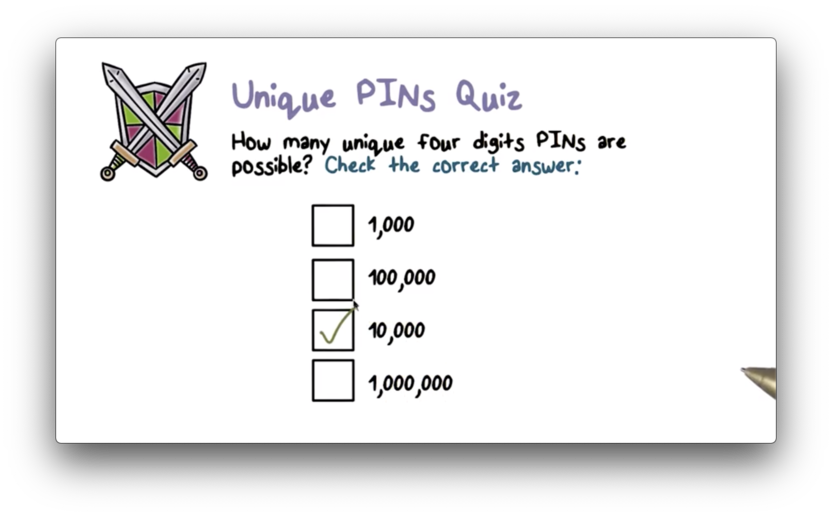
Unique PINS Quiz
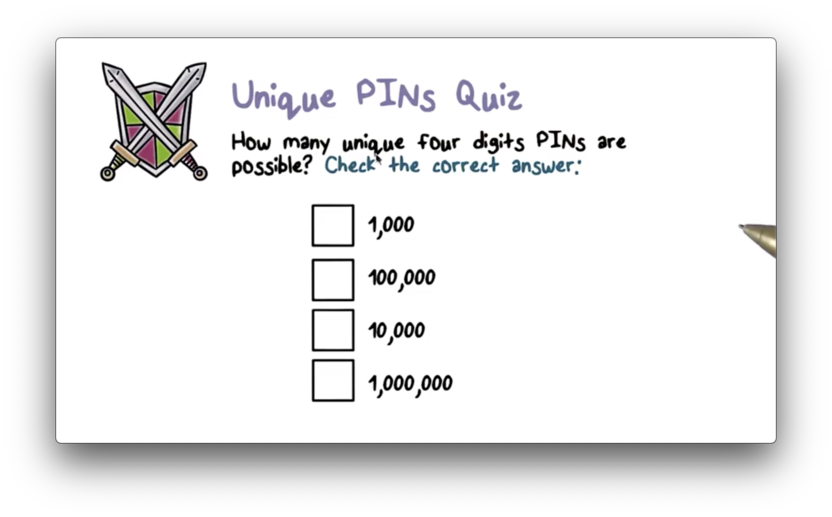
Unique PINS Quiz Solution
Brute Force Quiz

Brute Force Quiz Solution

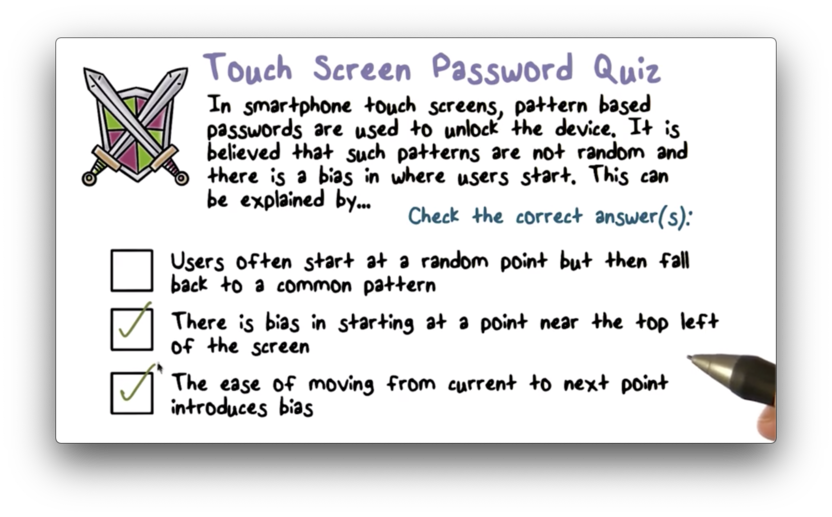
Touch Screen Passwords Quiz
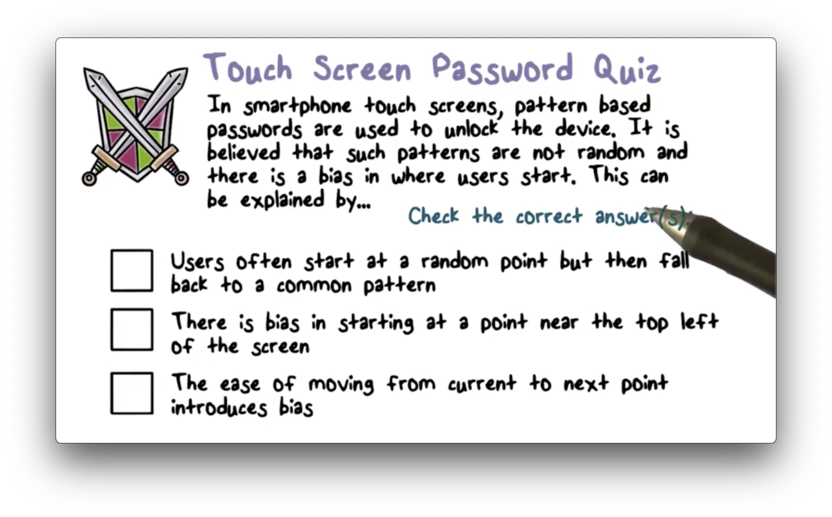
Touch Screen Passwords Quiz Solution
Multi-factor Authentication Quiz

Multi-factor Authentication Quiz Solution

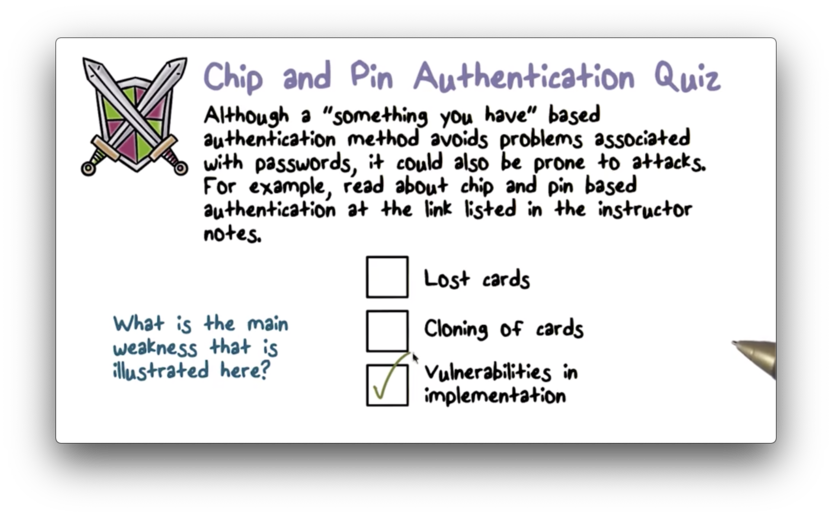
Chip and Pin Authentication Quiz
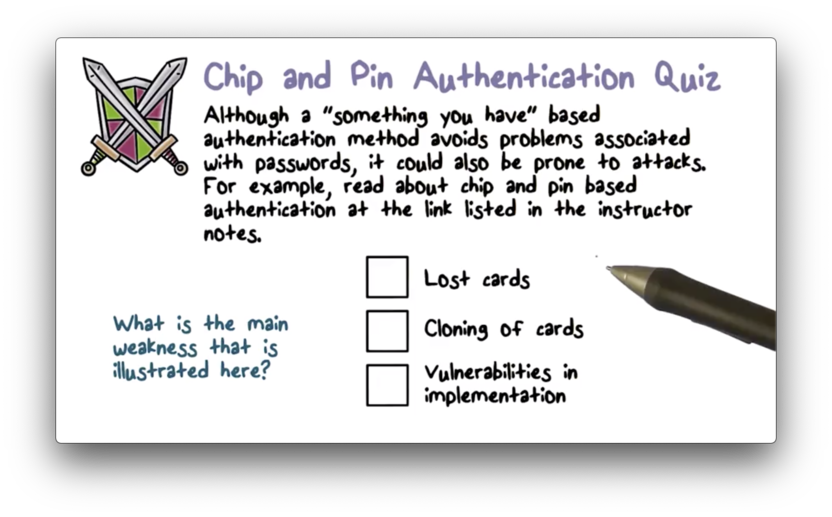
Chip and Pin Authentication Quiz Solution
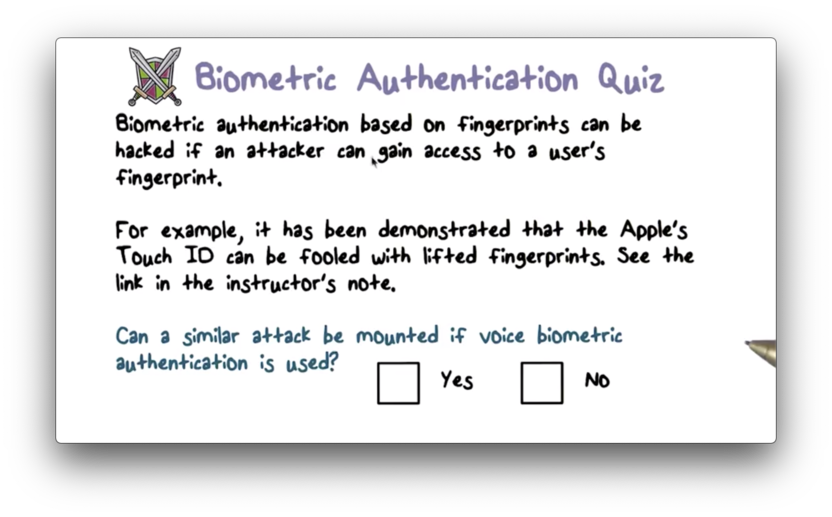
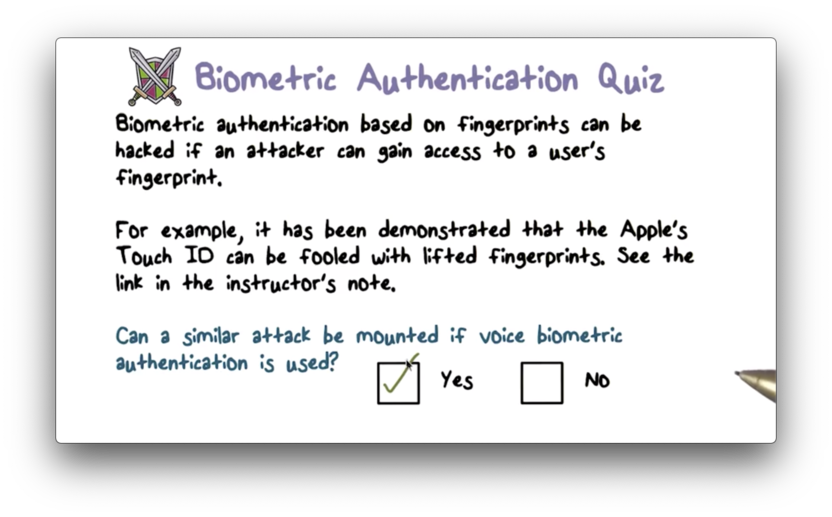
Biometric Authentication Quiz
Biometric Authentication Quiz Solution
Access Control
Data Confidentiality Quiz

Data Confidentiality Quiz Solution

Determining Access Quiz

Determining Access Quiz Solution

Discretionary Access Control Quiz

Discretionary Access Control Quiz Solution

ACE Quiz

ACE Quiz Solution
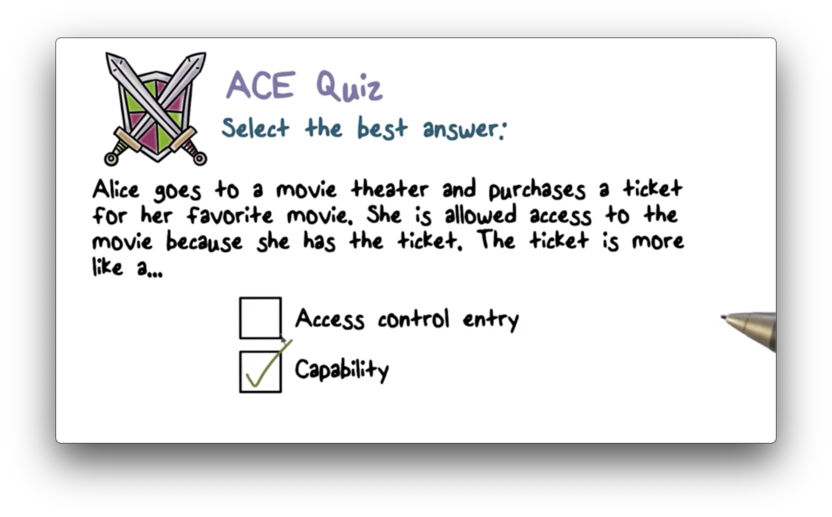
ACE Access Quiz

ACE Access Quiz Solution

Revocation of Rights Quiz
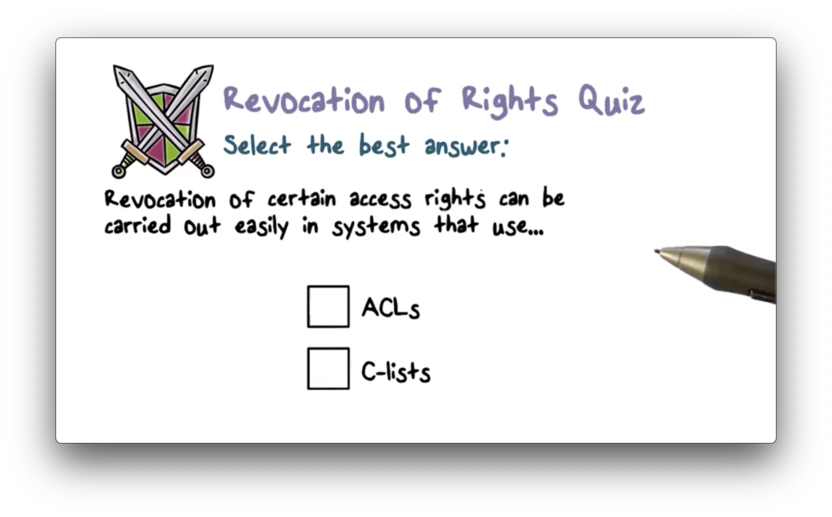
Revocation of Rights Quiz Solution

Time to Check vs Time to Use Quiz

Time to Check vs Time to Use Quiz Solution

Unix File Sharing Quiz

Unix File Sharing Quiz Solution

SetUID Bit Quiz

SetUID Bit Quiz Solution

RBAC Benefits Quiz

RBAC Benefits Quiz Solution

Access Control Policy Quiz

Access Control Policy Quiz Solution

Mandatory Access Control
DAC Quiz
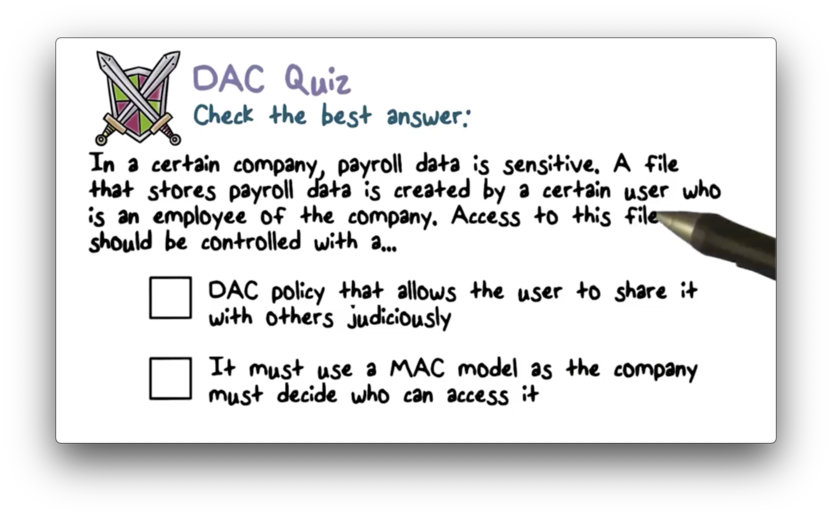
DAC Quiz Solution

Health Data Quiz

Health Data Quiz Solution

Security Clearance Quiz

Security Clearance Quiz Solution

Order Quiz

Order Quiz Solution

Label Domination Quiz

Label Domination Quiz Solution

Sensitive Data Quiz

Sensitive Data Quiz Solution

Unclassified Documents Quiz

Unclassified Documents Quiz Solution

Classified Data Quiz

Classified Data Quiz Solution

BLP Model Quiz

BLP Model Quiz Solution

Clark Wilson Quiz

Clark Wilson Quiz Solution

COI Quiz

COI Quiz Solution

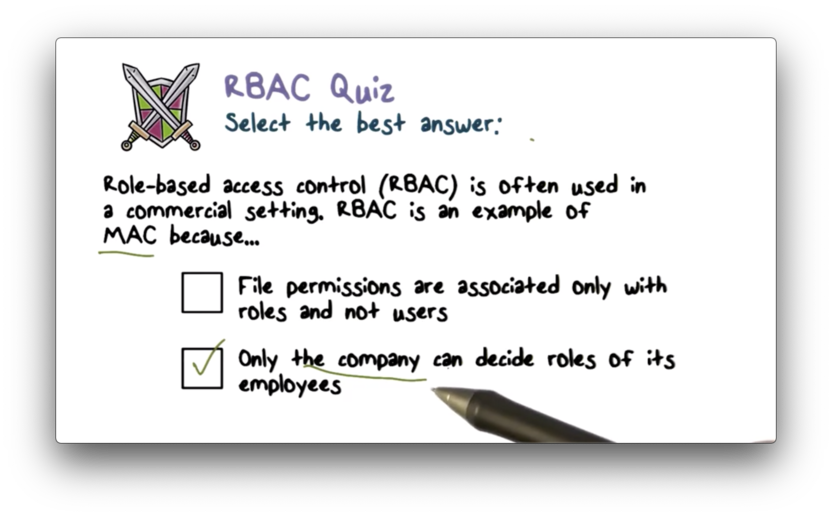
RBAC Quiz

RBAC Quiz Solution
MAC Support Quiz
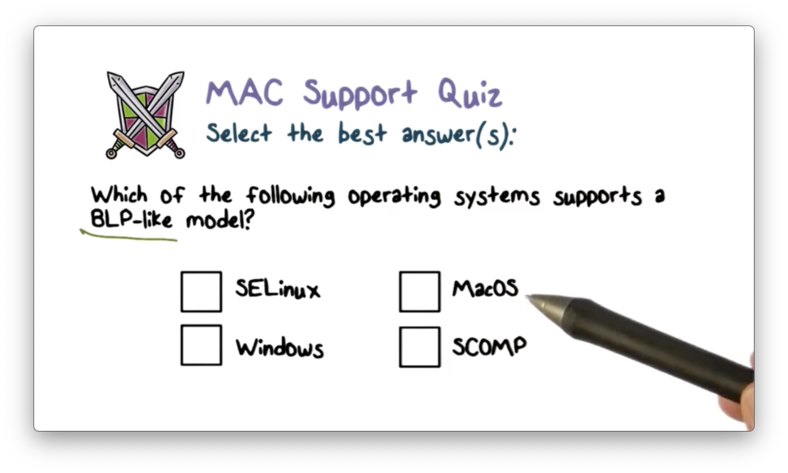
MAC Support Quiz Solution

Least Privilege Quiz

Least Privilege Quiz Solution

TCB High Assurance Quiz

TCB High Assurance Quiz Solution

Design Principle Quiz

Design Principle Quiz Solution

Reducing TCB Size Quiz

Reducing TCB Size Quiz Solution

Testing TCB Quiz

Testing TCB Quiz Solution

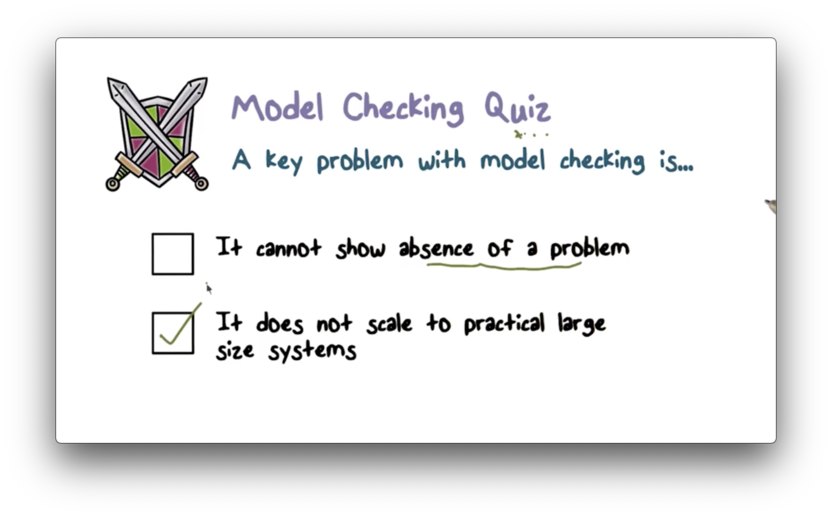
Model Checking Quiz

Model Checking Quiz Solution
TCSEC Divisions Quiz

TCSEC Divisions Quiz Solution

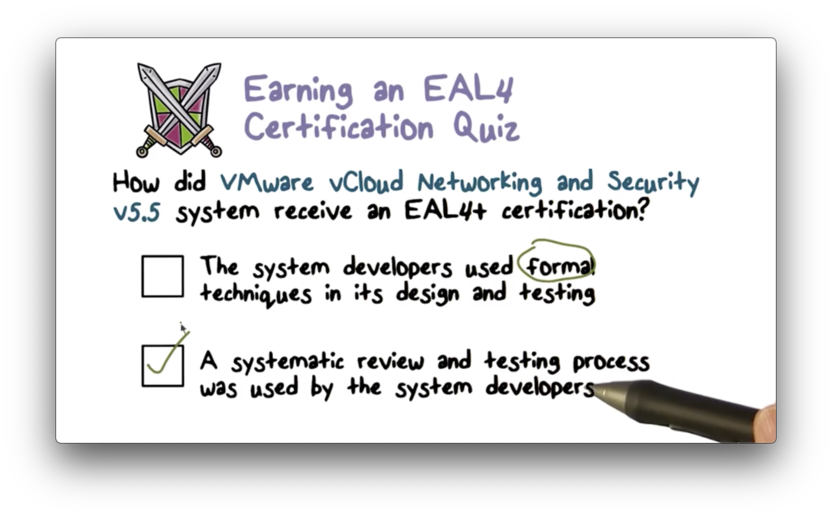
Earning an EAL4 Certification Quiz

Earning an EAL4 Certification Quiz Solution
Cost Benefit Certification Tradeoffs Quiz

Cost Benefit Certification Tradeoffs Quiz Solution

Database Security
Database Threats Quiz

Database Threats Quiz Solution

Database Hacking Quiz

Database Hacking Quiz Solution

Key Value Quiz

Key Value Quiz Solution

Database Views Quiz

Database Views Quiz Solution

Database Access Control Quiz

Database Access Control Quiz Solution

Cascading Authorizations Quiz

Cascading Authorizations Quiz Solution

DAC or MAC Quiz

DAC or MAC Quiz Solution

SQL Login Quiz

SQL Login Quiz Solution

SQL Login Quiz 2

SQL Login Quiz 2 Solution

SQL Inference Attack Quiz

SQL Inference Attack Quiz Solution

SQL Inference Attack Quiz 2

SQL Inference Attack Quiz 2 Solution

Malicious Code
What is Malware Quiz

What is Malware Quiz Solution

Host Required Malware Quiz 1

Host Required Malware Quiz 1 Solution

Host Required Malware Quiz 2

Host Required Malware Quiz 2 Solution

Types of Viruses Quiz

Types of Viruses Quiz Solution

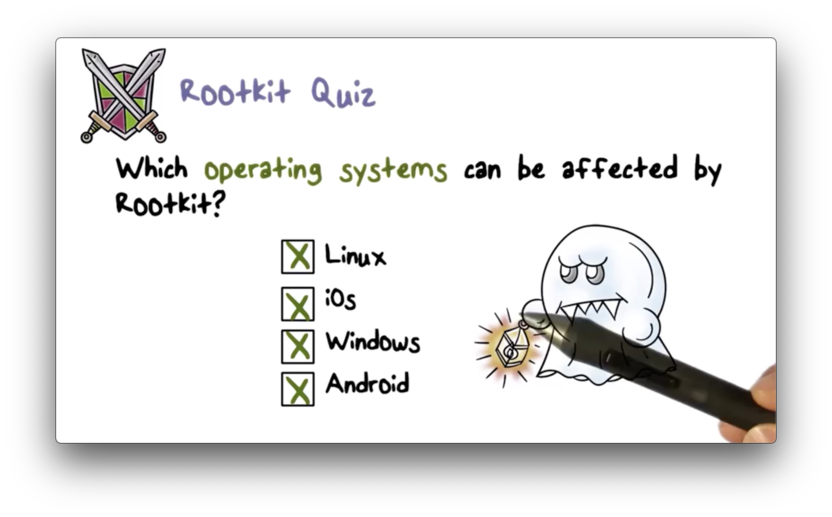
Rootkit Quiz
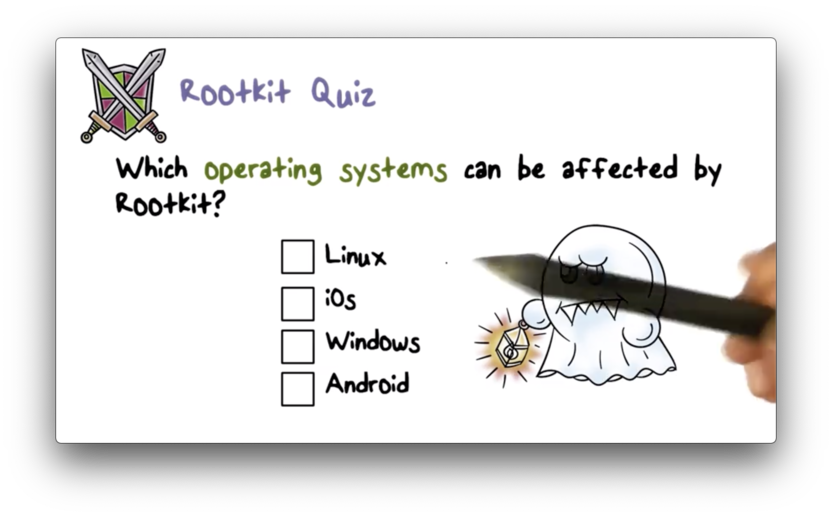
Rootkit Quiz Solution
Truth and Misconceptions Quiz

Truth and Misconceptions Quiz Solution

Worm Quiz

Worm Quiz Solution

Malware Prevention & Detection Quiz

Malware Prevention & Detection Quiz Solution

Most Expensive Worm Quiz

Most Expensive Worm Quiz Solution

Modern Malware
Bot Quiz

Bot Quiz Solution

DDoS Quiz

DDoS Quiz Solution

C&C Design Quiz

C&C Design Quiz Solution

Botnet C&C Quiz

Botnet C&C Quiz Solution

APT Quiz

APT Quiz Solution

Malware Analysis Quiz

Malware Analysis Quiz Solution

Firewalls
Firewalls Quiz

Firewalls Quiz Solution

Firewall Features Quiz
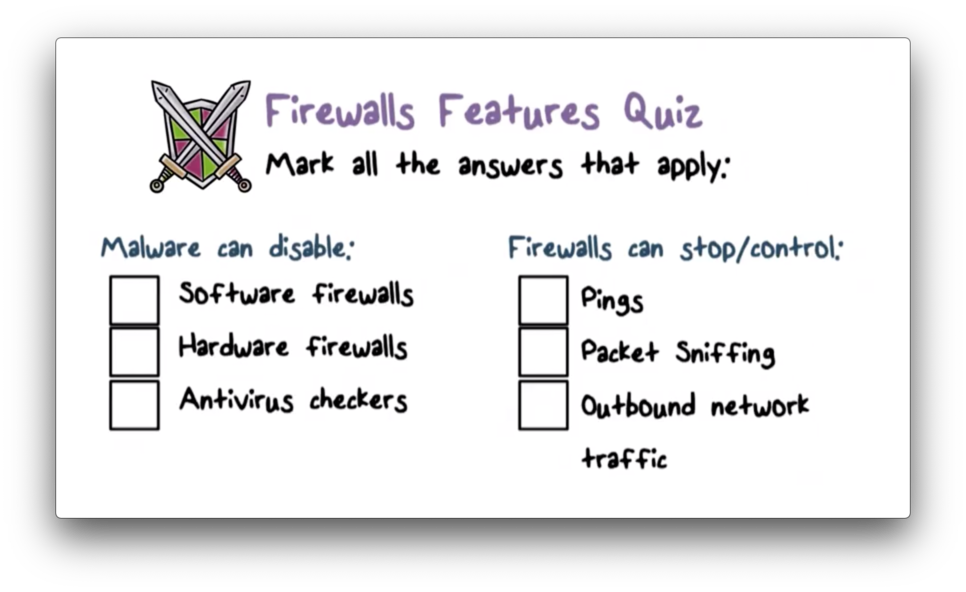
Firewall Features Quiz Solution

Firewall Filtering Quiz
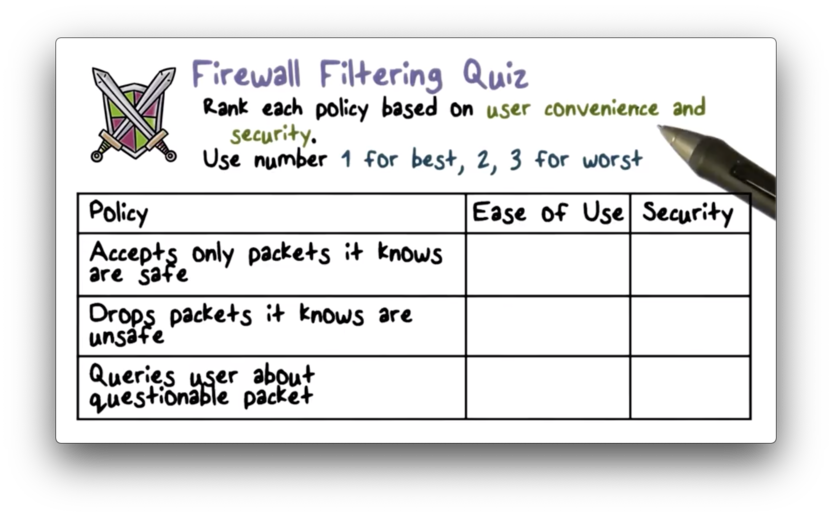
Firewall Filtering Quiz Solution

Packet Filtering Quiz

Packet Filtering Quiz Solution

Filtering Quiz

Filtering Quiz Solution

Personal Firewalls Quiz

Personal Firewalls Quiz Solution

Firewall Deployment Quiz

Firewall Deployment Quiz Solution

Stand Alone Firewall Quiz

Stand Alone Firewall Quiz Solution

Intrusion Detection
Intrusion Detection Quiz

Intrusion Detection Quiz Solution

Intruder Quiz

Intruder Quiz Solution

Types of Backdoors Quiz

Types of Backdoors Quiz Solution

Analysis Detection Quiz

Analysis Detection Quiz Solution

Signature Detection Quiz

Signature Detection Quiz Solution

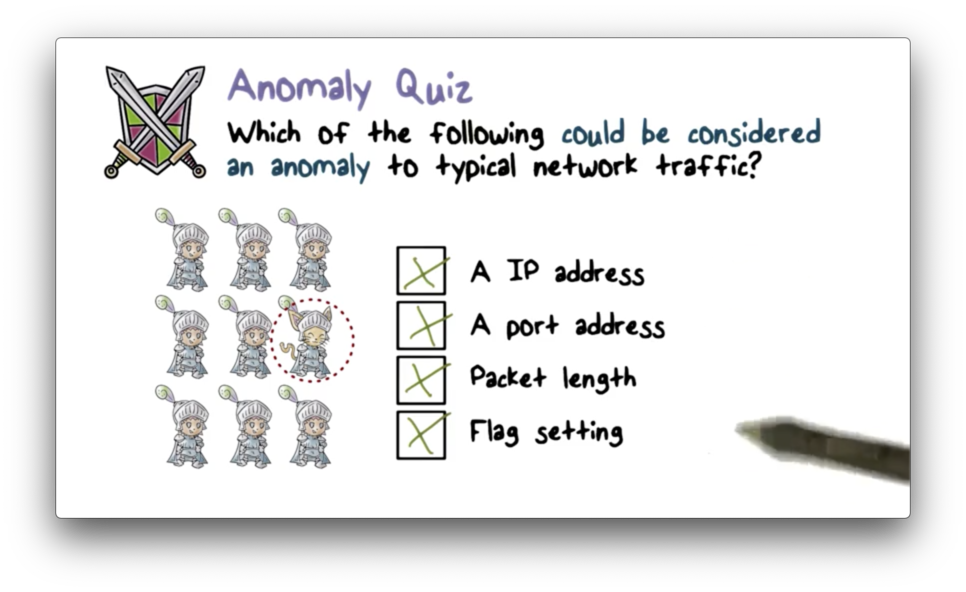
Anomaly Quiz
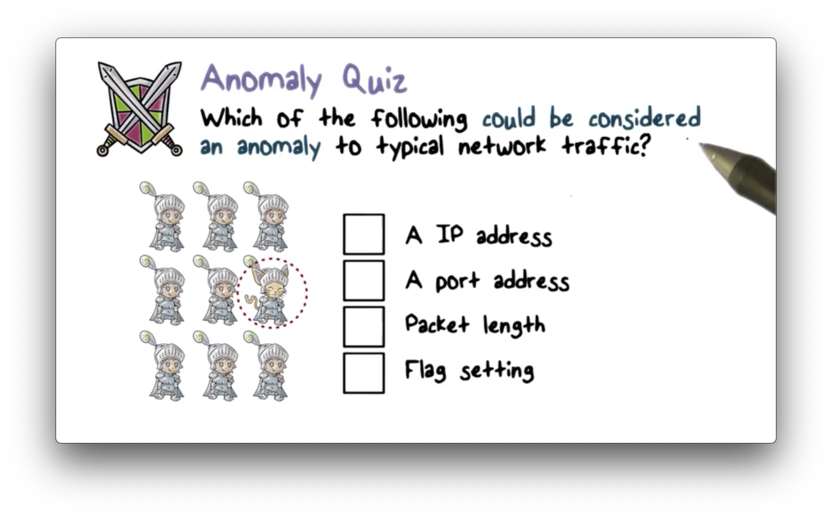
Anomaly Quiz Solution
Statistical & Knowledge Based Approaches Quiz

Statistical & Knowledge Based Approaches Quiz Solution

Machine Learning Quiz

Machine Learning Quiz Solution

Anomalous Behavior Quiz

Anomalous Behavior Quiz Solution

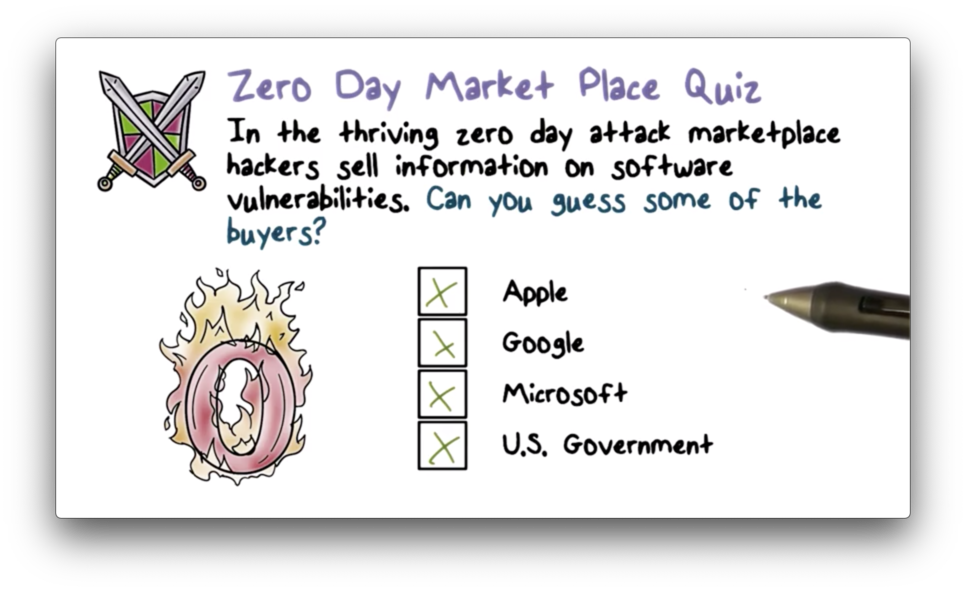
Zero Day Market Place Quiz

Zero Day Market Place Quiz Solution
Attacks Quiz

Attacks Quiz Solution

NIDS Quiz

NIDS Quiz Solution

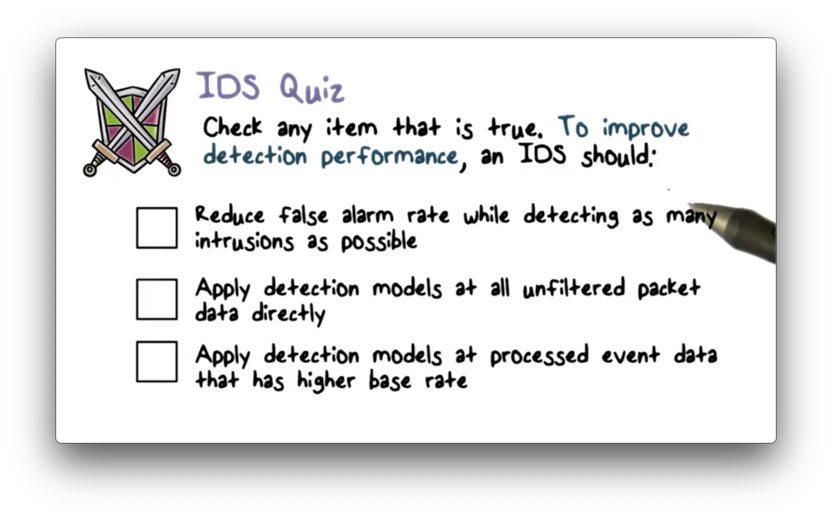
IDS Quiz

IDS Quiz Solution

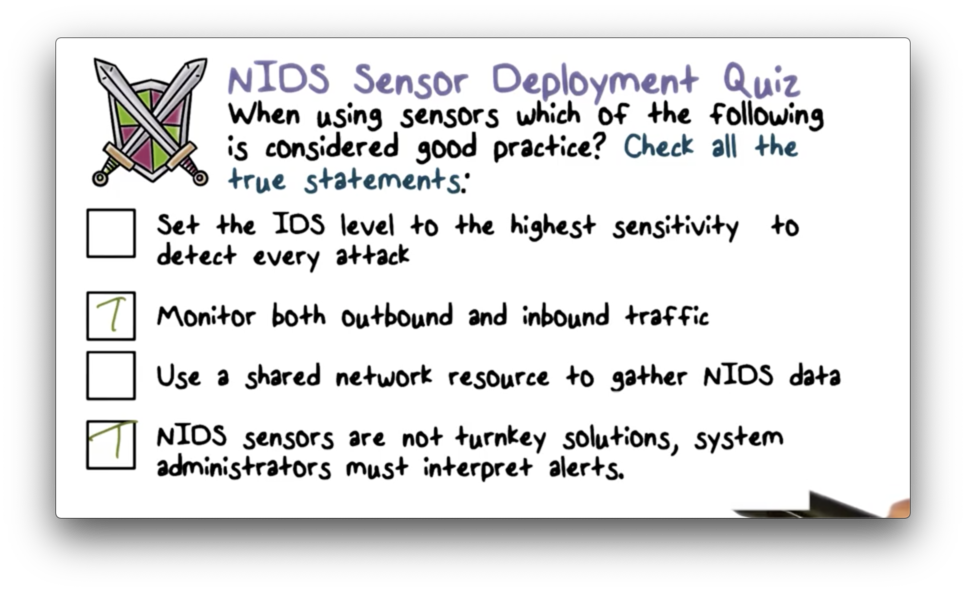
NIDS Sensor Deployed Quiz
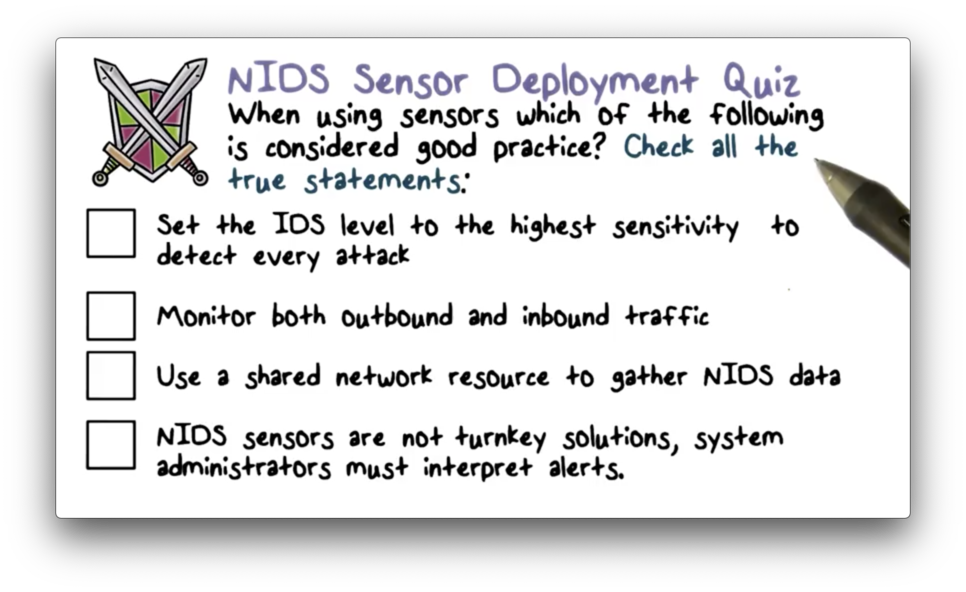
NIDS Sensor Deployed Quiz Solution
Snort Quiz

Snort Quiz Solution

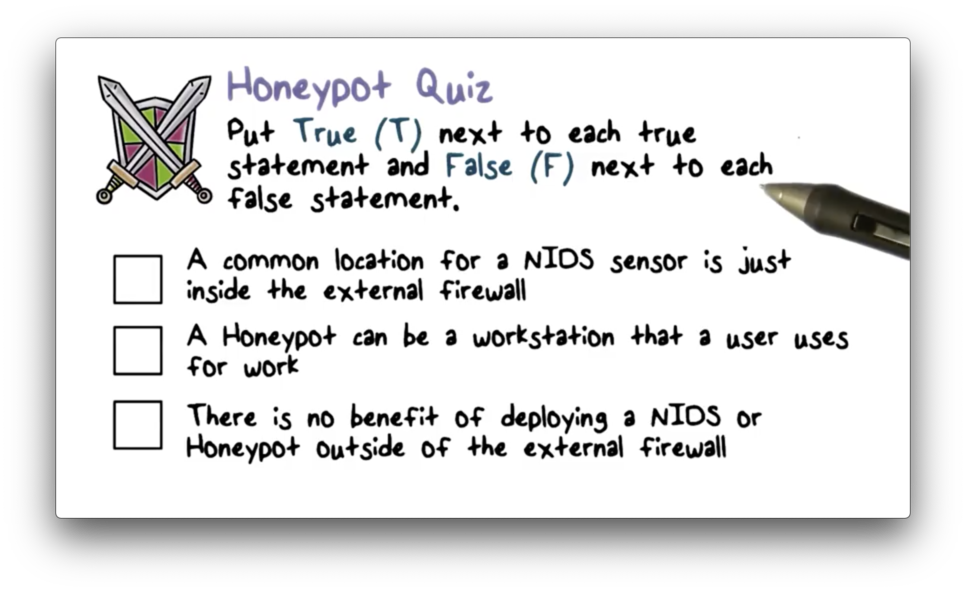
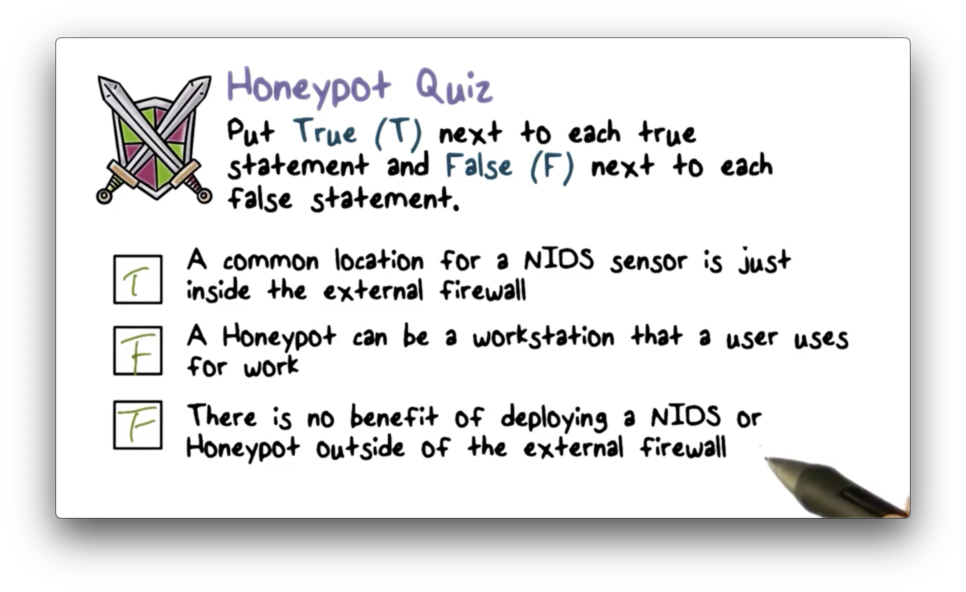
Honeypot Quiz
Honeypot Quiz Solution
IDS Quiz
IDS Quiz Solution

IDS Attack Quiz

IDS Attack Quiz Solution

Introduction to Cryptography
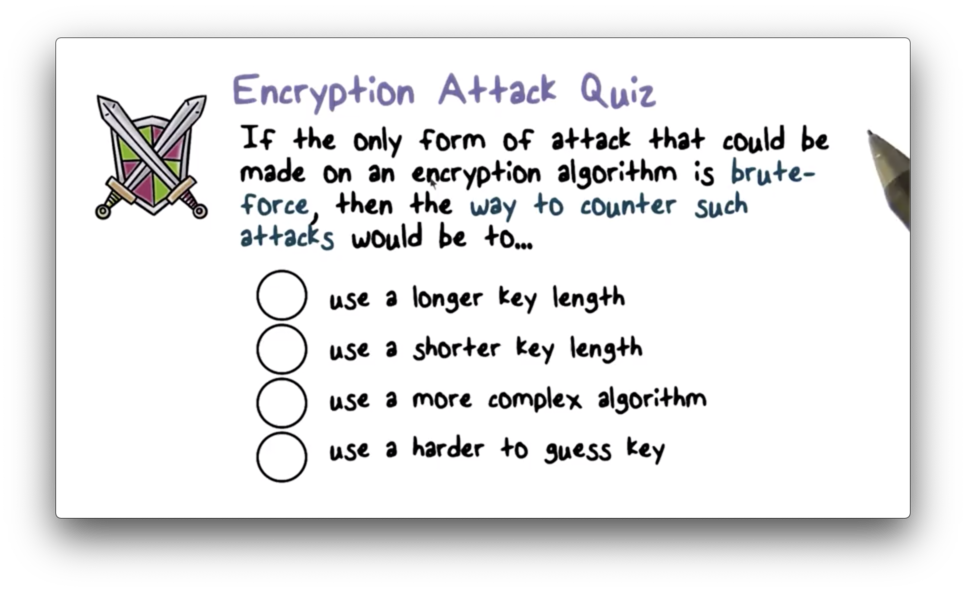
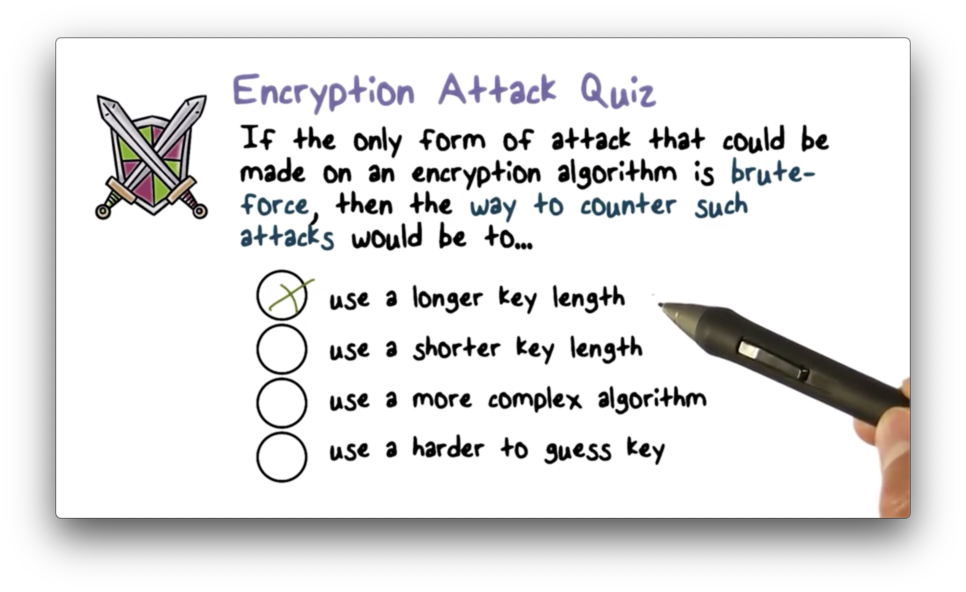
Encryption Attack Quiz
Encryption Attack Quiz Solution
Simple Ciphers Quiz

Simple Ciphers Quiz Solution

Monoalphabetic Cipher Quiz

Monoalphabetic Cipher Quiz Solution

Vigenere Cipher Quiz

Vigenere Cipher Quiz Solution

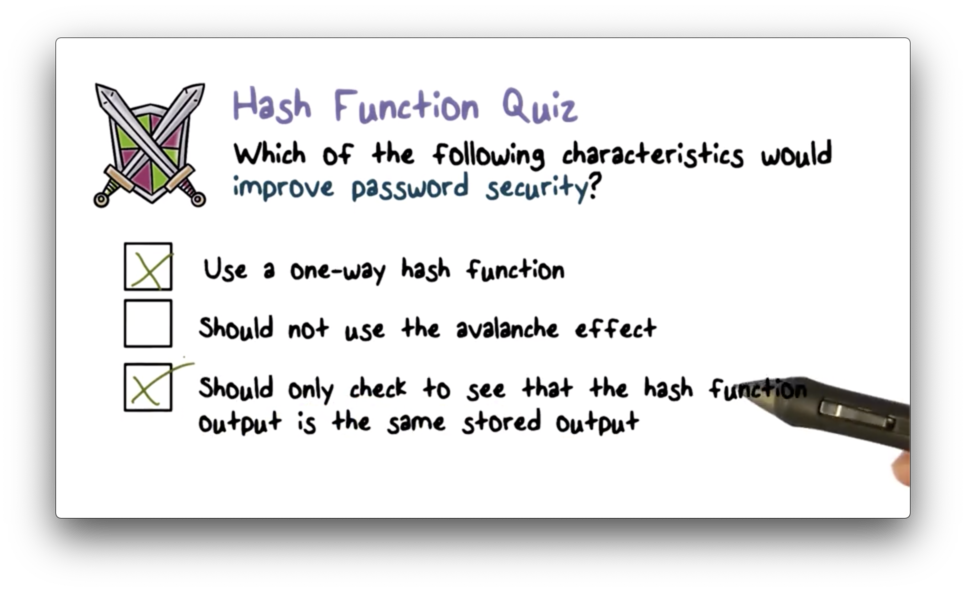
Hash Function Quiz
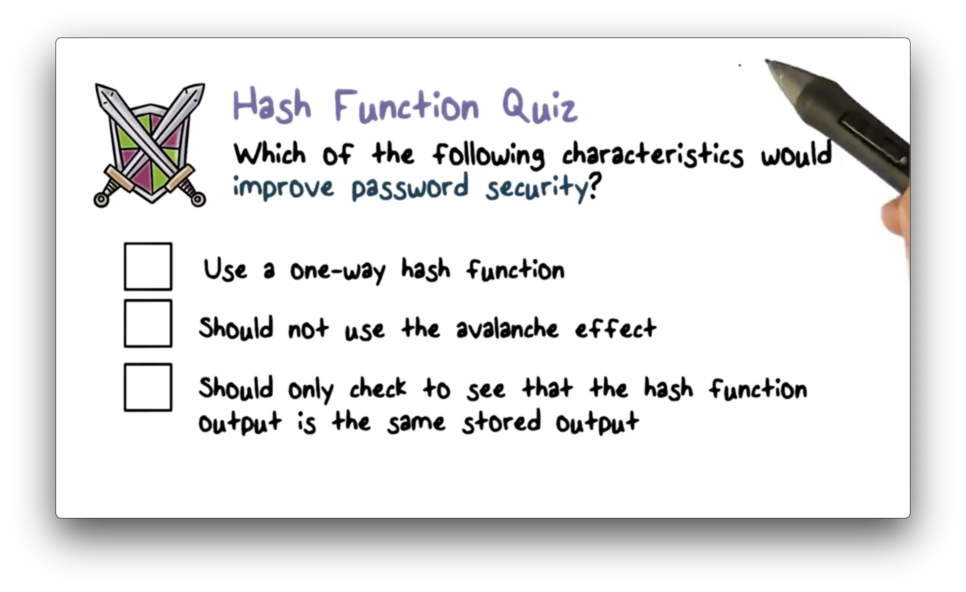
Hash Function Quiz Solution
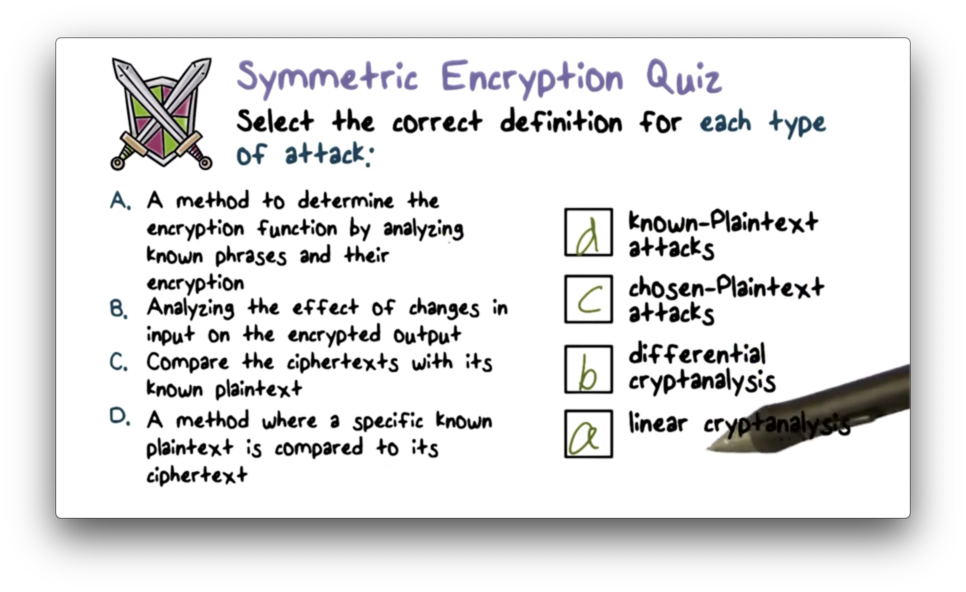
Symmetric Encryption Quiz

Symmetric Encryption Quiz Solution
Asymmetric Encryption Quiz

Asymmetric Encryption Quiz Solution

Encryption Quiz

Encryption Quiz Solution

Symmetric Encryption
Block Cipher Quiz

Block Cipher Quiz Solution

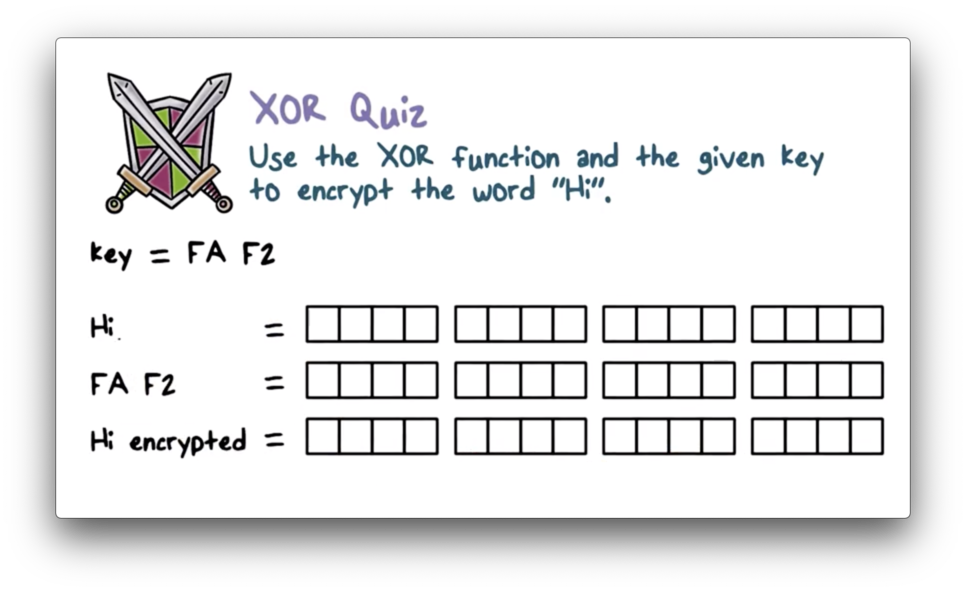
XOR Quiz
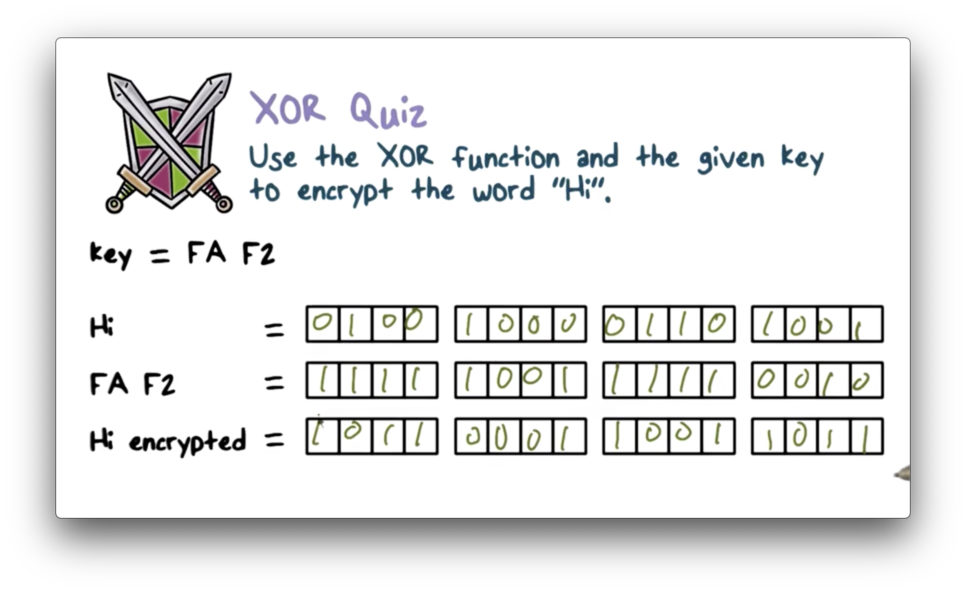
XOR Quiz Solution
S Box Quiz

S Box Quiz Solution

DES Quiz

DES Quiz Solution

AES Encryption Quiz

AES Encryption Quiz Solution

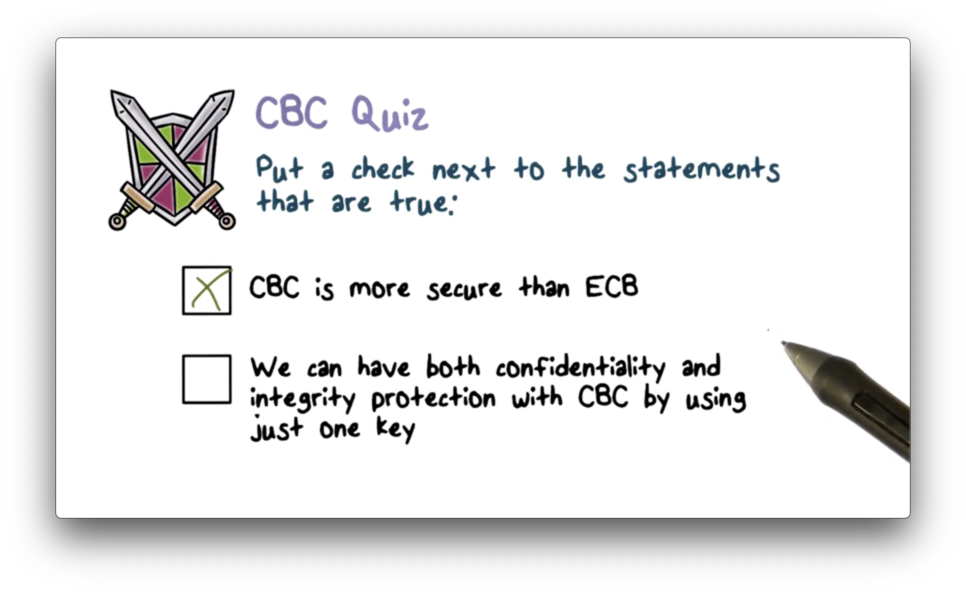
CBC Quiz

CBC Quiz Solution
Public-Key Cryptography
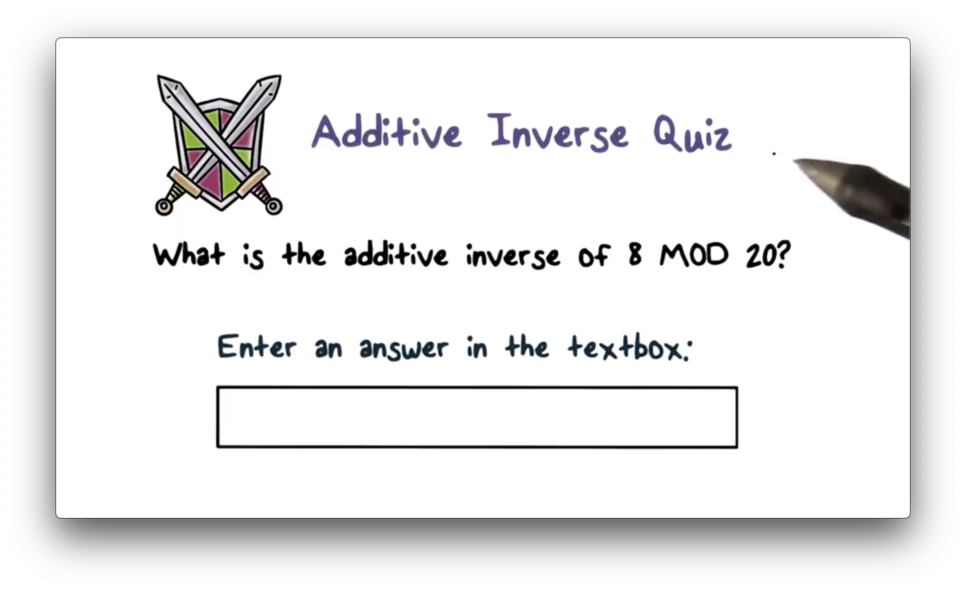
Additive Inverse Quiz
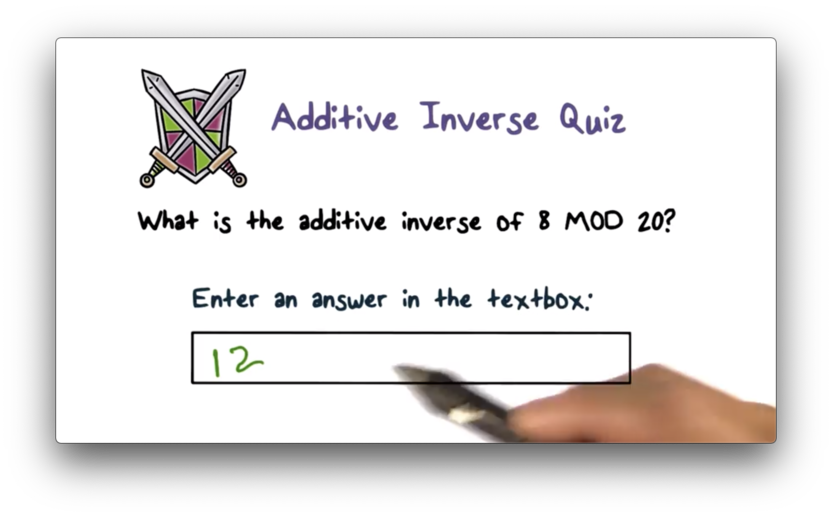
Additive Inverse Quiz Solution
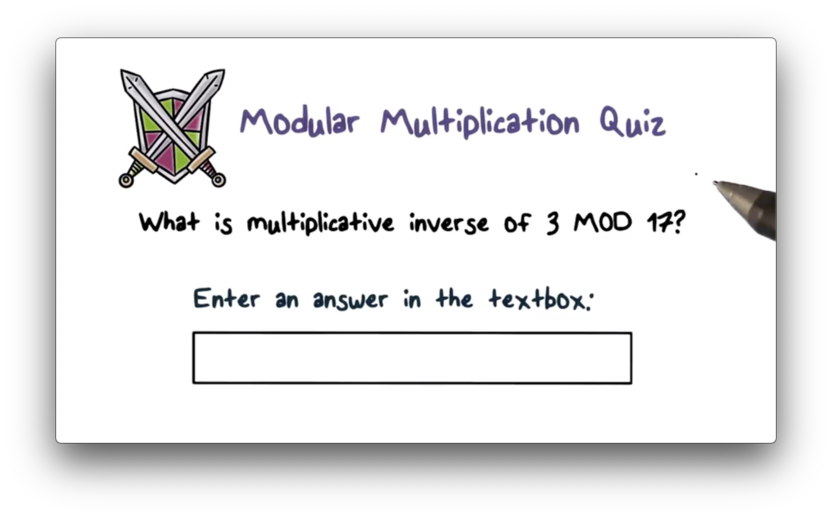
Modular Multiplication Quiz
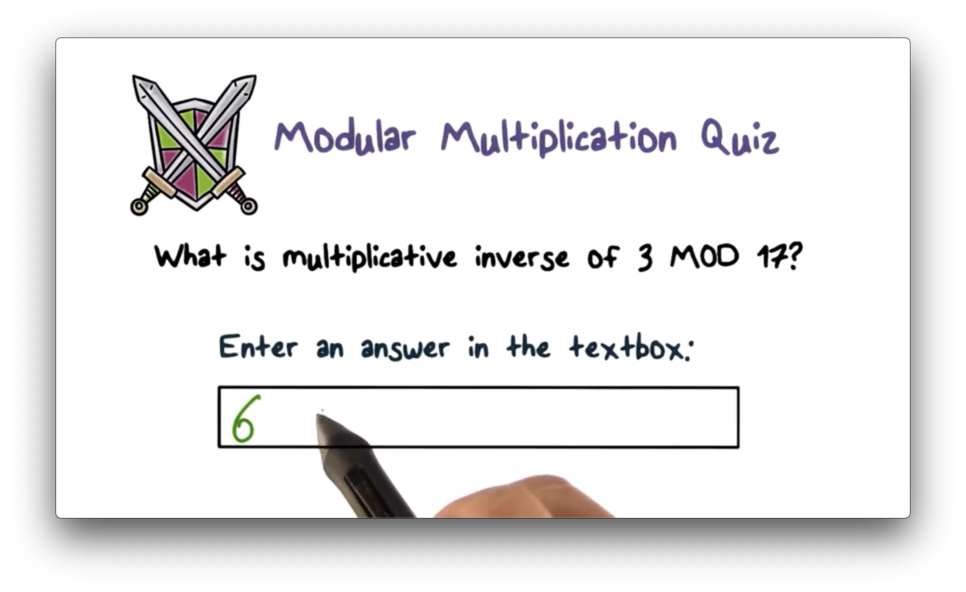
Modular Multiplication Quiz Solution
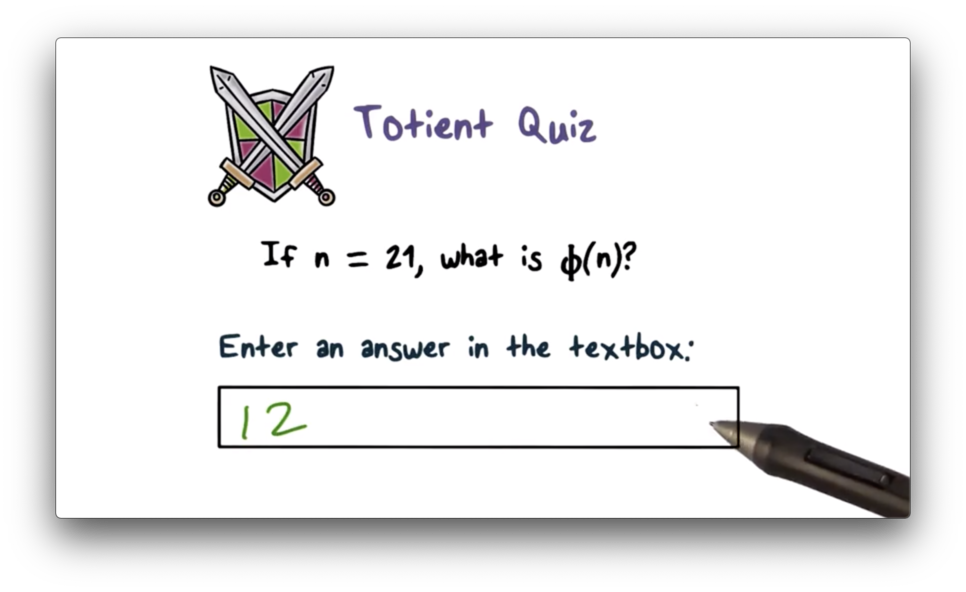
Totient Quiz

Totient Quiz Solution
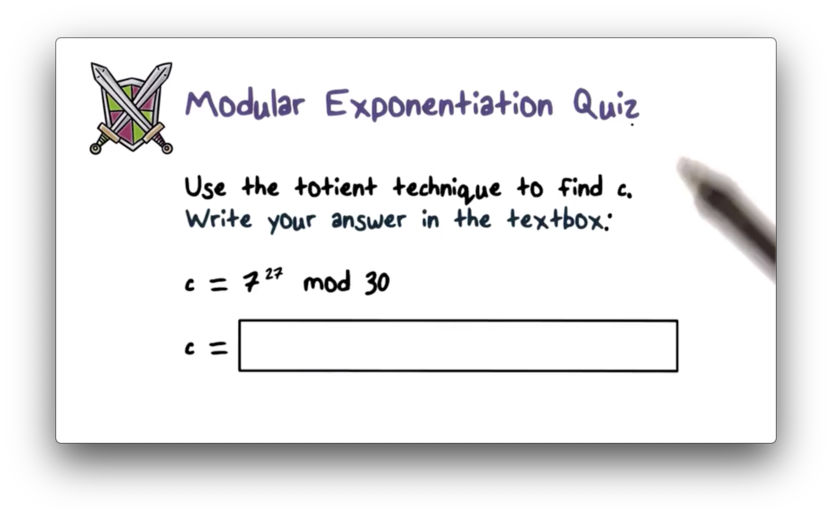
Modular Exponentiation Quiz
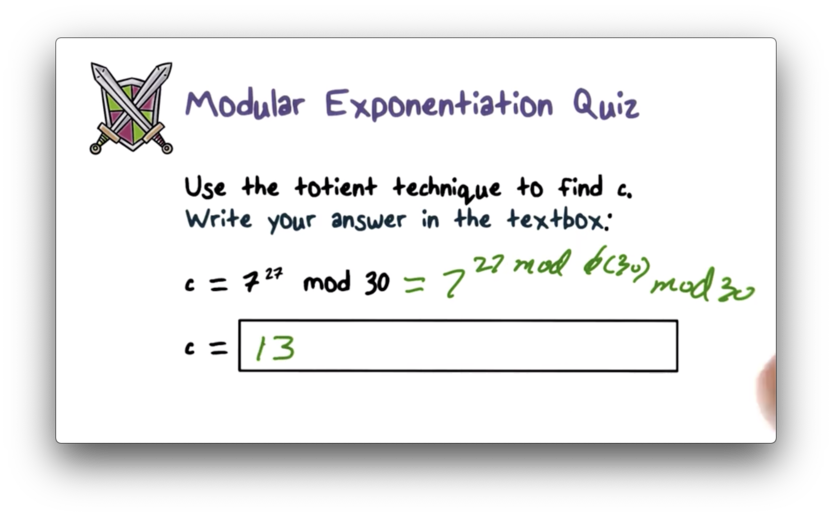
Modular Exponentiation Quiz Solution
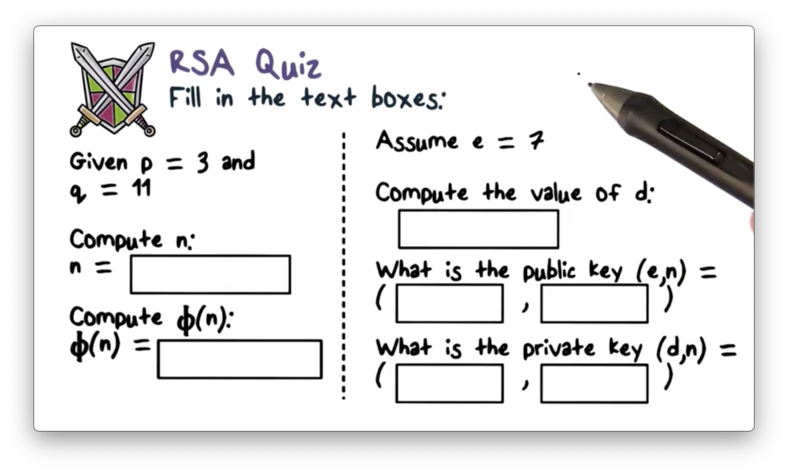
RSA Quiz
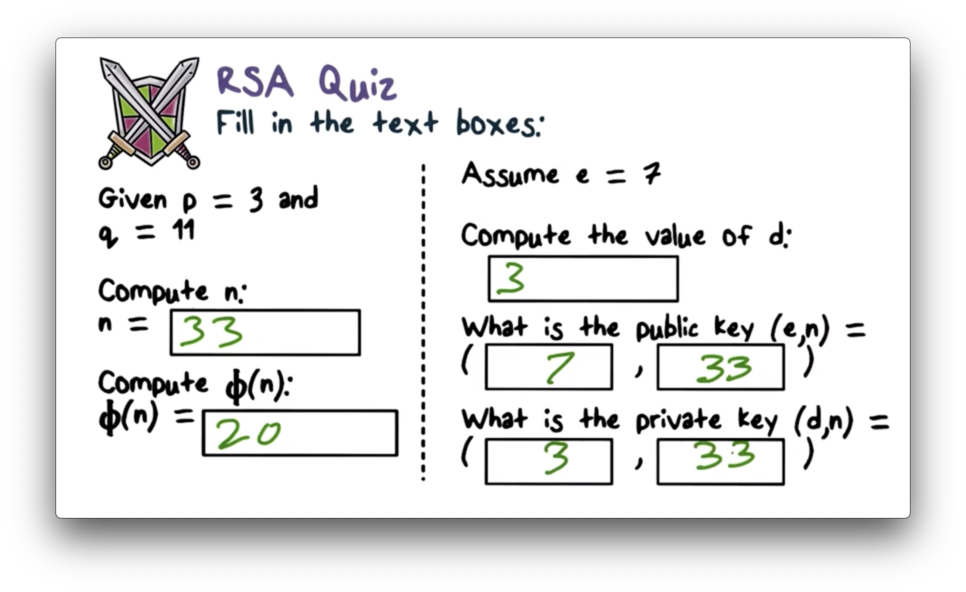
RSA Quiz Solution
RSA Encryption Quiz

RSA Encryption Quiz Solution

RSA in Practice Quiz

RSA in Practice Quiz Solution

Diffie-Hellman Quiz
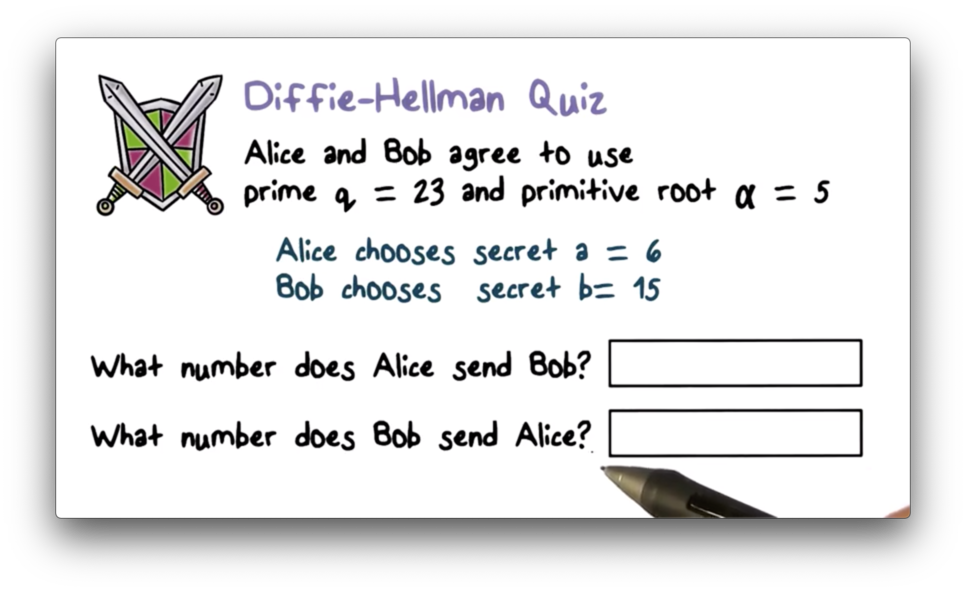
Diffie-Hellman Quiz Solution

RSA, Diffie-Hellman Quiz

RSA, Diffie-Hellman Quiz Solution

Hashes
Hash Size Quiz
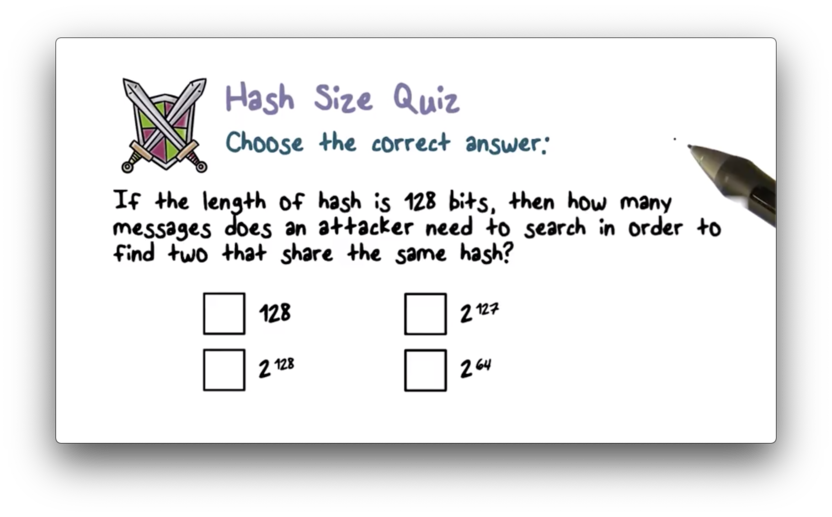
Hash Size Quiz Solution

Hash Function Quiz

Hash Function Quiz Solution

Security Protocols
Mutual Authentication Quiz

Mutual Authentication Quiz Solution

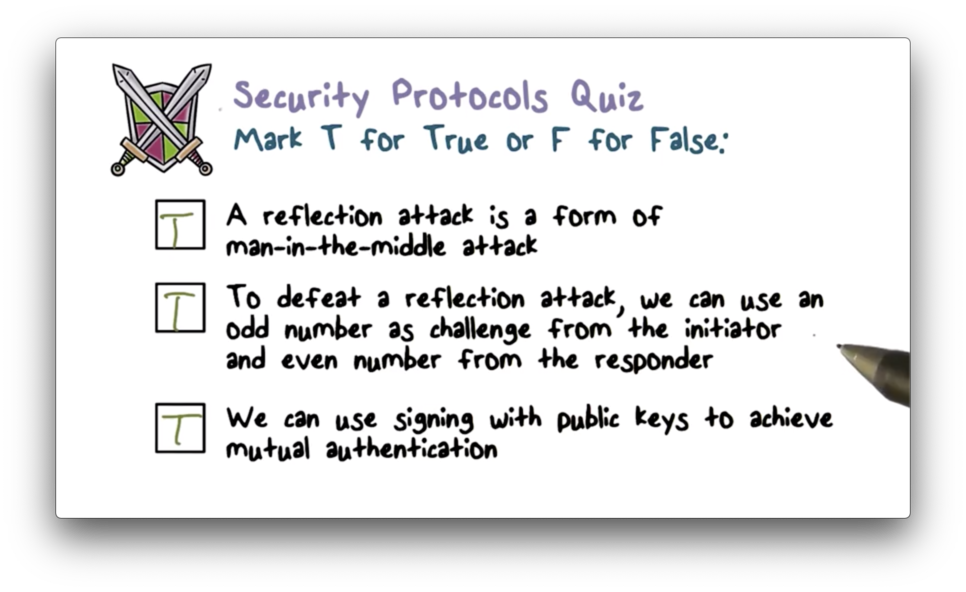
Security Protocols Quiz
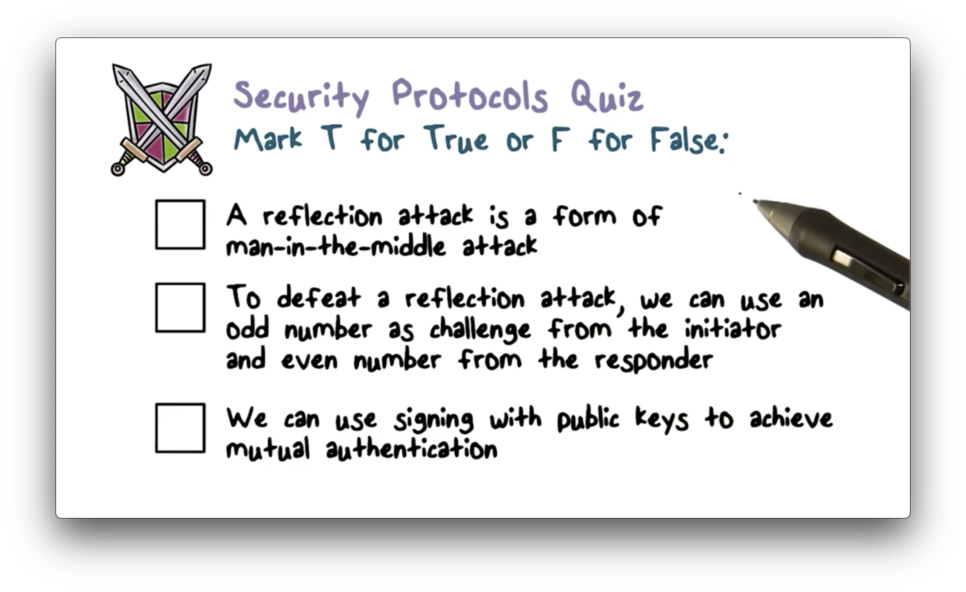
Security Protocols Quiz Solution
Session Key Quiz

Session Key Quiz Solution

Kerberos Quiz

Kerberos Quiz Solution

IPSec and TLS
Spoofing Quiz

Spoofing Quiz Solution

IPSec Quiz

IPSec Quiz Solution

ESP Modes Quiz

ESP Modes Quiz Solution

ESP and AH Quiz

ESP and AH Quiz Solution

IPSec Quiz

IPSec Quiz Solution

Diffie Hellman Quiz

Diffie Hellman Quiz Solution

IKE Quiz

IKE Quiz Solution

TLS and SSL Quiz

TLS and SSL Quiz Solution

Wireless and Mobile Security
Wifi Quiz
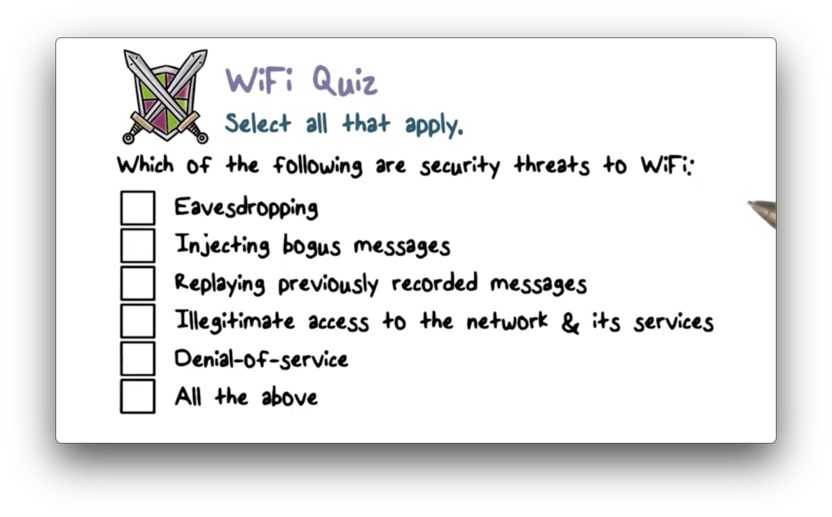
Wifi Quiz Solution

Wifi Security Standards Quiz

Wifi Security Standards Quiz Solution

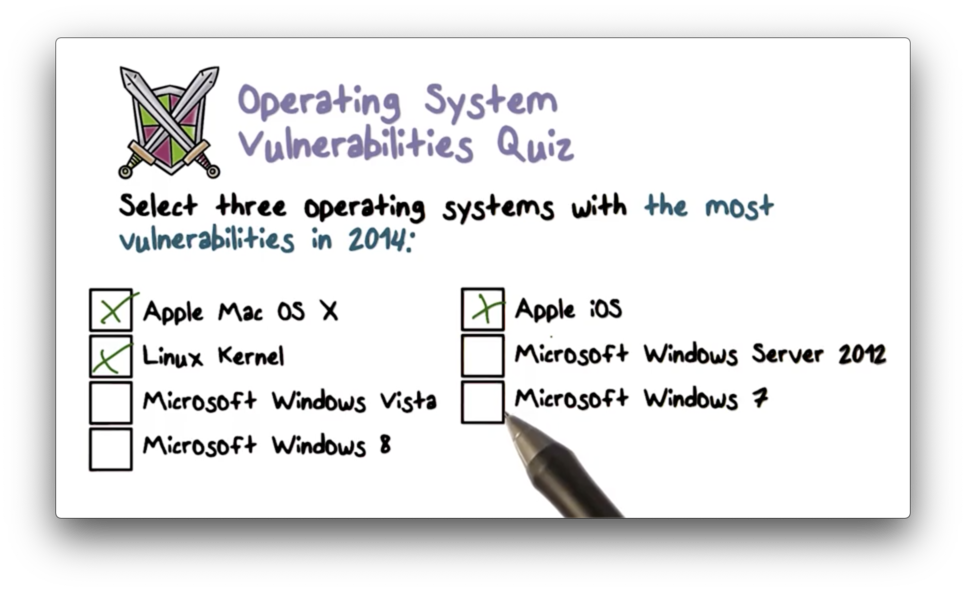
Operating System Vulnerabilities Quiz
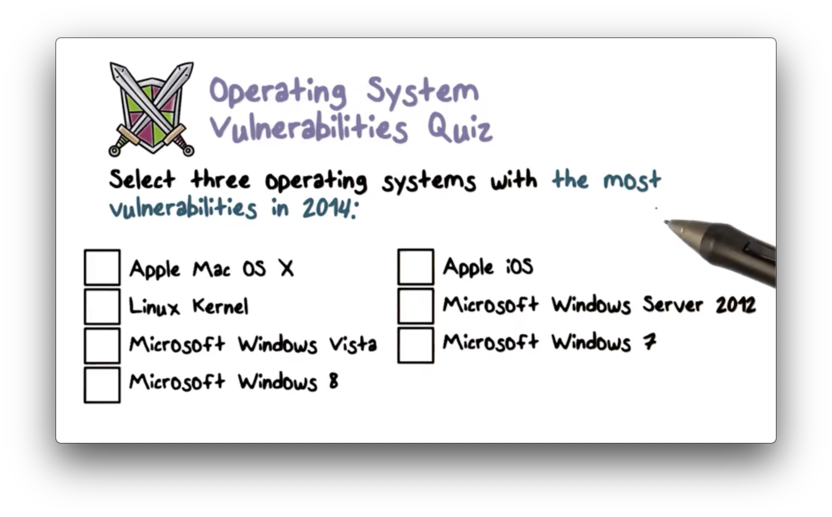
Operating System Vulnerabilities Quiz Solution
Security Quiz

Security Quiz Solution

App Store Security Quiz
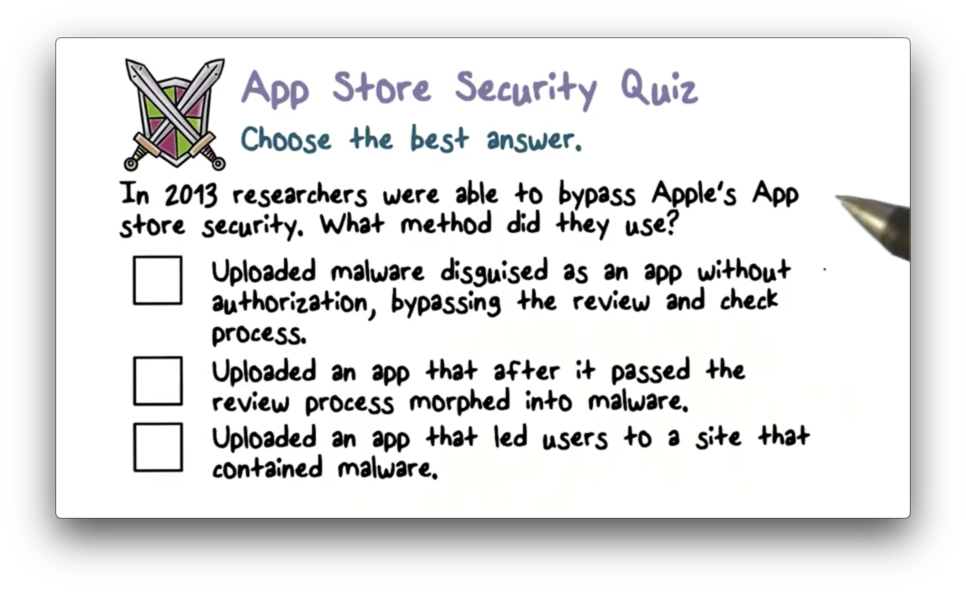
App Store Security Quiz Solution
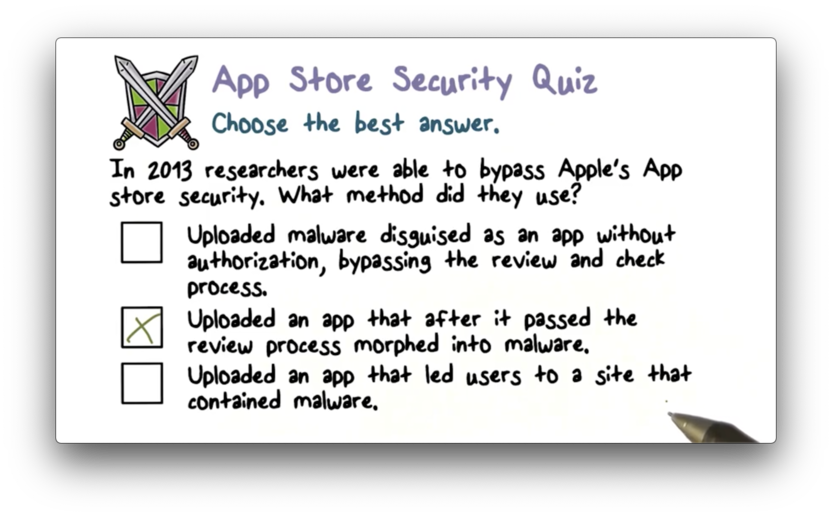
iOS Security Quiz
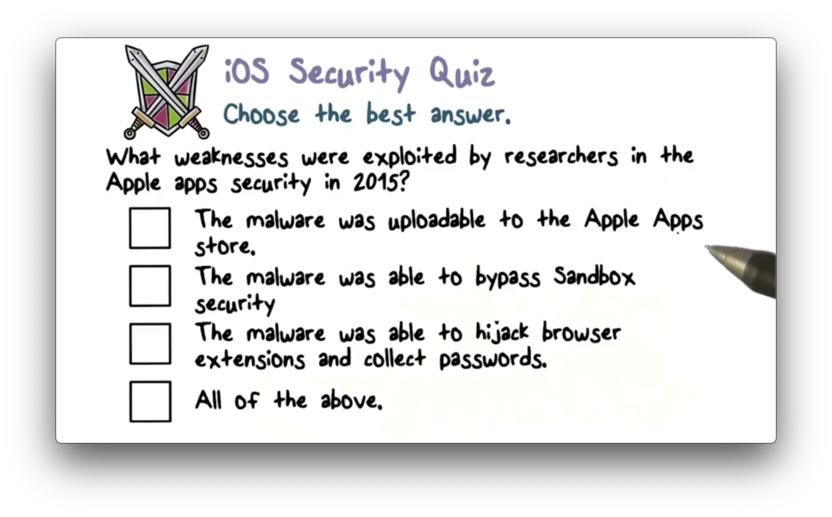
iOS Security Quiz Solution

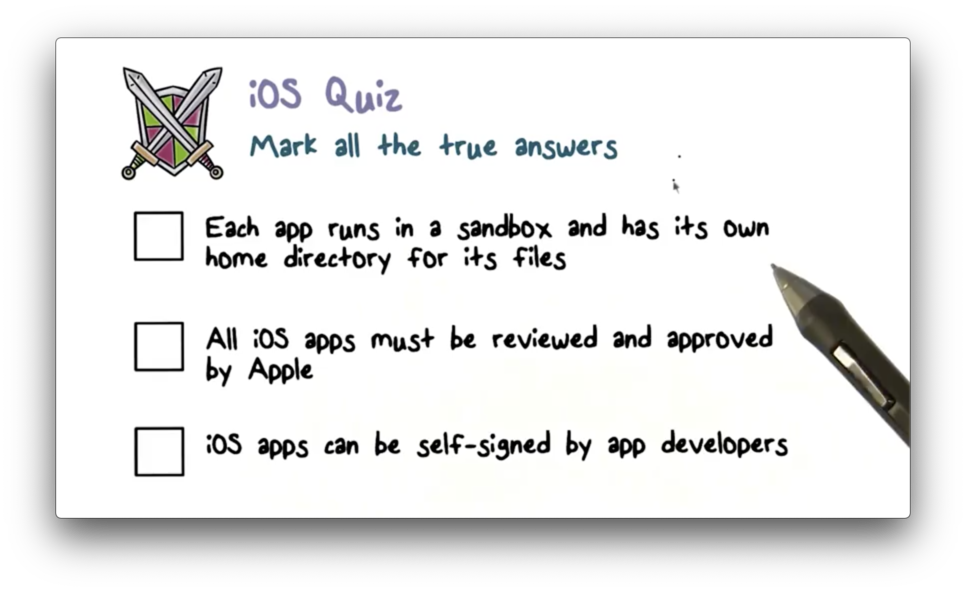
iOS Quiz
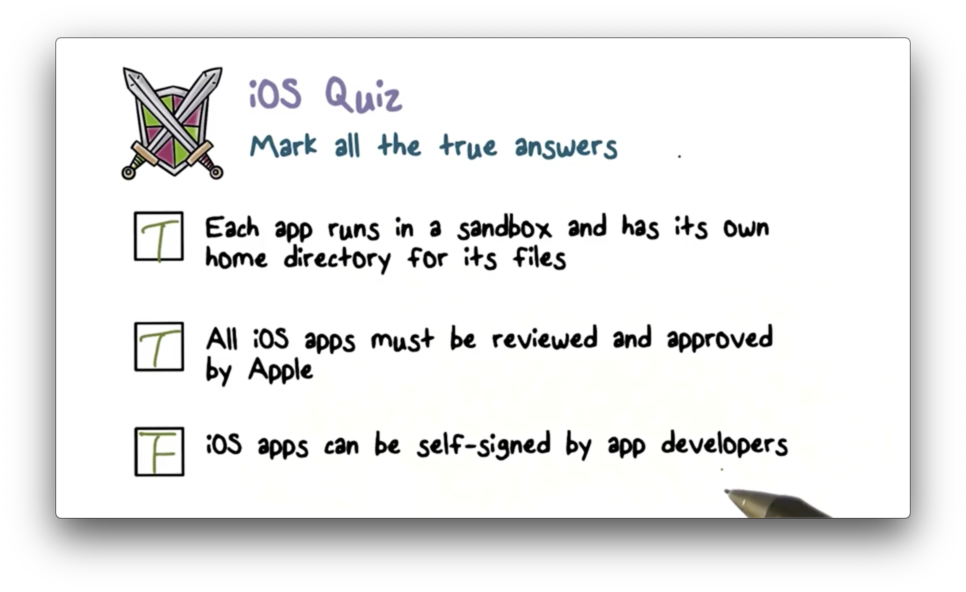
iOS Quiz Solution
Android Apps Quiz

Android Apps Quiz Solution

Web Security
Cookie Quiz

Cookie Quiz Solution

Web Security Quiz

Web Security Quiz Solution

XSS Quiz

XSS Quiz Solution

XSRF Quiz

XSRF Quiz Solution

SQL Injection Quiz

SQL Injection Quiz Solution

Cyber Security
Network Use Policy Quiz

Network Use Policy Quiz Solution

Botnet Quiz

Botnet Quiz Solution

Security Audit Quiz

Security Audit Quiz Solution

CISO Quiz

CISO Quiz Solution

Computer Use Policy Quiz

Computer Use Policy Quiz Solution

Student Privacy Quiz

Student Privacy Quiz Solution

Anthem Breach Quiz

Anthem Breach Quiz Solution

Security Breach Quiz

Security Breach Quiz Solution

Reducing Exposure Quiz

Reducing Exposure Quiz Solution

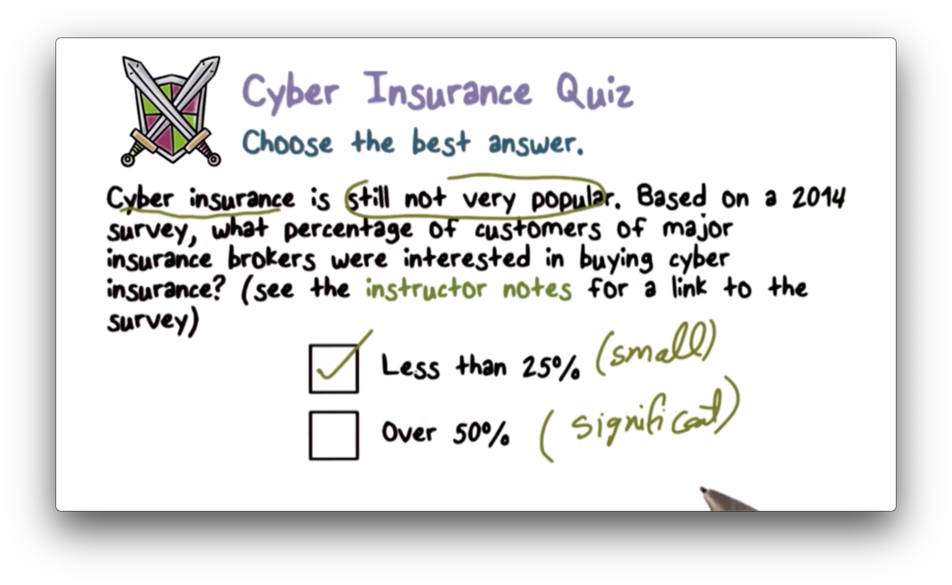
Cyber Insurance Quiz

Cyber Insurance Quiz Solution
Cyber Security Budgets Quiz

Cyber Security Budgets Quiz Solution

Proactive Security Quiz

Proactive Security Quiz Solution

Law, Ethics, and Privacy
Legal Deterrents Quiz

Legal Deterrents Quiz Solution

Cost of Cybercrime Quiz

Cost of Cybercrime Quiz Solution

Melissa Virus Quiz

Melissa Virus Quiz Solution

Unauthorized Access Quiz

Unauthorized Access Quiz Solution

DMCA Exclusions Quiz

DMCA Exclusions Quiz Solution

Computer Ethics Quiz

Computer Ethics Quiz Solution

Responsible Disclosure Quiz

Responsible Disclosure Quiz Solution

Privacy Quiz

Privacy Quiz Solution

Right to Be Forgotten Quiz

Right to Be Forgotten Quiz Solution

EFF Quiz

EFF Quiz Solution

Google Privacy Policy Quiz

Google Privacy Policy Quiz Solution

Legal Deterrents Quiz

Legal Deterrents Quiz Solution

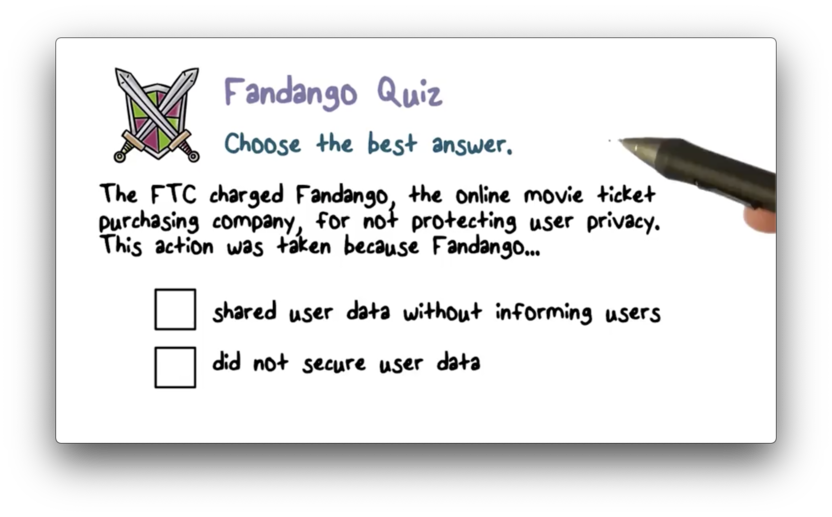
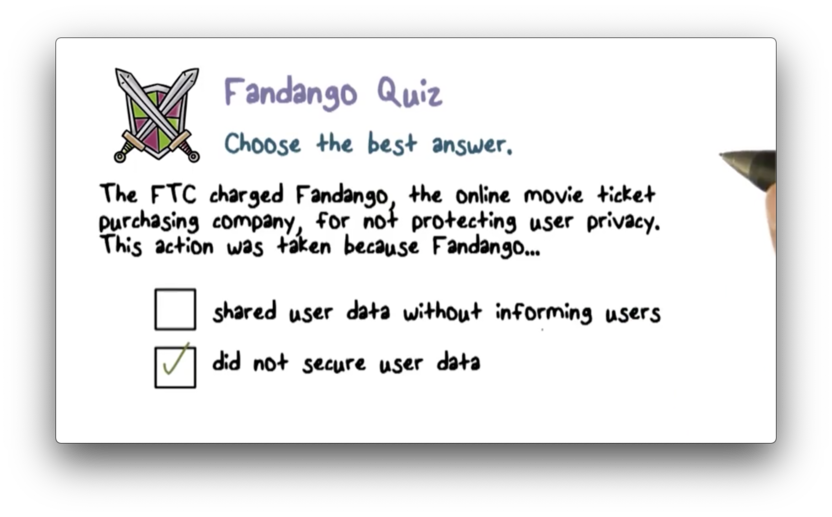
Fandango Quiz
Fandango Quiz Solution
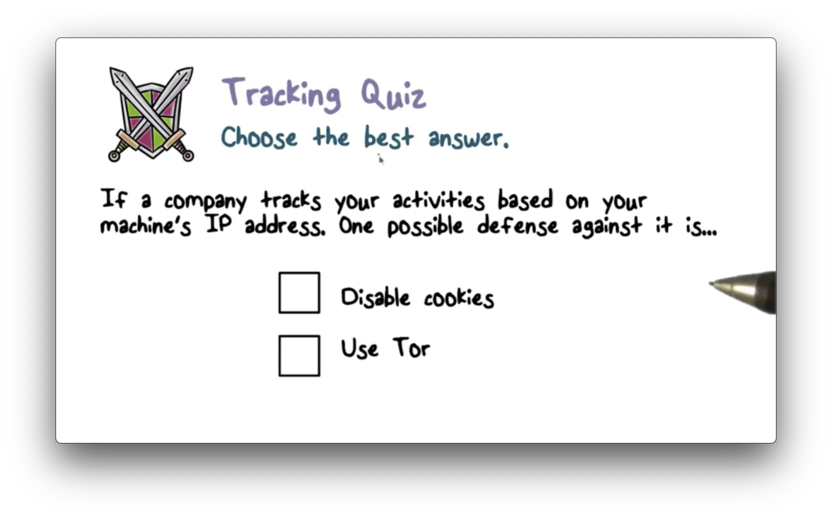
Tracking Quiz
Tracking Quiz Solution
Last updated